Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@Jadx MCP Servershow me the decompiled source code for MainActivity"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
⚙️ Jadx MCP Plugin — Decompiler Access for Claude via MCP
This project provides a Jadx plugin written in Java, which exposes the Jadx API over HTTP — enabling live interaction through MCP clients like Claude via the Model Context Protocol (MCP). A lightweight FastMCP adapter in Python acts as a bridge between Claude and the plugin. This enables intelligent navigation and automation of reverse engineering workflows, ideal for AI-assisted security analysis of Android apps.
🧰 Setup Instructions
Install Python dependencies
🧠 Setup Claude MCP CLient Integration
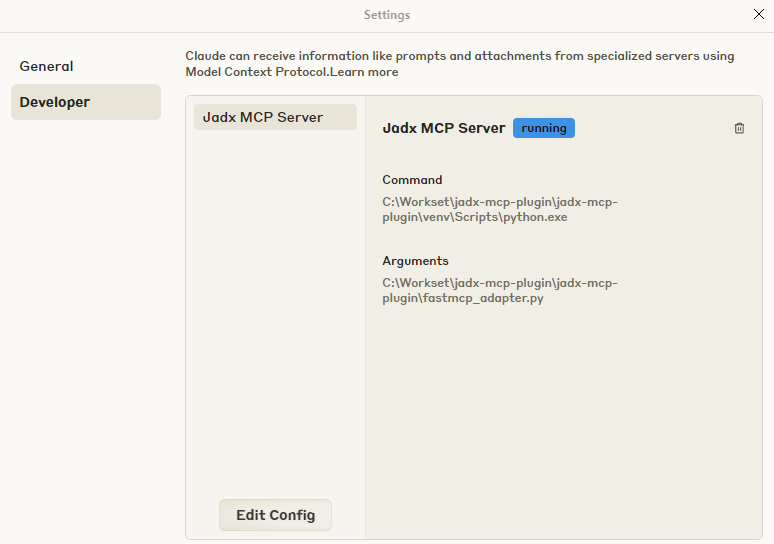
To use this adapter in Claude Desktop, go to File -> Settings -> Developer -> Edit Config -> claude_desktop_config.json and add an MCP server pointing to the Python executable in the venv (to prevent depedency issues) and the full adapter path following below examples:
Windows:
MacOS / Linux:
Make sure to restart (Quit) Claude after editing the config.
After restart it should look like this:
✅ Usage Flow
Open Jadx with the latest plugin JAR from the releases placed in its
plugins/folder or load it viaPlugins->install plugin.Load an APK or DEX file
(Optional) You can specify the HTTP interface address by launching Jadx with:
jadx-gui -Pjadx-mcp.http-interface=http://localhost:8085This is useful if you want to change the default host/port (
http://localhost:8085).Note: If you change the interface address here, make sure to also update the corresponding URL in
fastmcp_adapter.pyto match.Claude will detect and activate the Jadx MCP Server tools.
You can now list classes, fetch source, inspect methods/fields, and extract code live.
Related MCP server: Coder Toolbox MCP Server
🧪 Tools Provided
Tool | Description |
| Get all decompiled class names |
| Find classes matching a string |
| Get full source of a given class |
| Find methods matching a string |
| List all method names in a class |
| List all field names in a class |
| Extract decompiled code for a method |
🛠 Development
☕ Java Plugin
The Java plugin is located at:
It uses the JadxPlugin API (jadx.api.*) to:
Load decompiled classes and methods
Serve structured data via an embedded HTTP server
Respond to
/invokeand/toolsendpoints
🚀 Automated Installation with Gradle Tasks
You can use the following Gradle task to build and install the plugin in one step:
This uses the
jadx pluginsCLI. Make sure Jadx is installed and available in yourPATH.
For other plugin-related tasks (uninstall, enable/disable), see the task definitions in plugin/build.gradle.
🔧 Manual Installation
To build the plugin:
Install the plugin JAR using the jadx plugins CLI:
Alternatively, place the built .jar file into your Jadx plugins/ folder, typically located at: ~/.jadx/plugins/
If you place the JAR manually, you’ll also need to enable the plugin through the Jadx GUI or by running:
Python FastMCP Adapter
The adapter file is:
It translates Claude’s MCP tool calls into HTTP POSTs to the running Jadx plugin server. Make sure Jadx is open before starting Claude.
🤝 Contributing
PRs, feature requests, and tool extensions are welcome!
This project is maintained by Mobile Hacking Lab.