Handles configuration through environment variables stored in a .env file, specifically for storing sudo passwords needed for bpftrace execution
Enables tracing and monitoring of the Linux kernel using eBPF technology through bpftrace, allowing for performance analysis, debugging, and observability of kernel functions and system calls
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@bpftrace MCP Servertrace which processes are opening files right now"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
bpftrace MCP Server: generate eBPF to trace linux kernel
A minimal MCP (Model Context Protocol) server that provides AI assistants with access to bpftrace kernel tracing capabilities.
Now implemented in Rust using the rmcp crate for better performance and type safety. The Python implementation is still available in the git history.
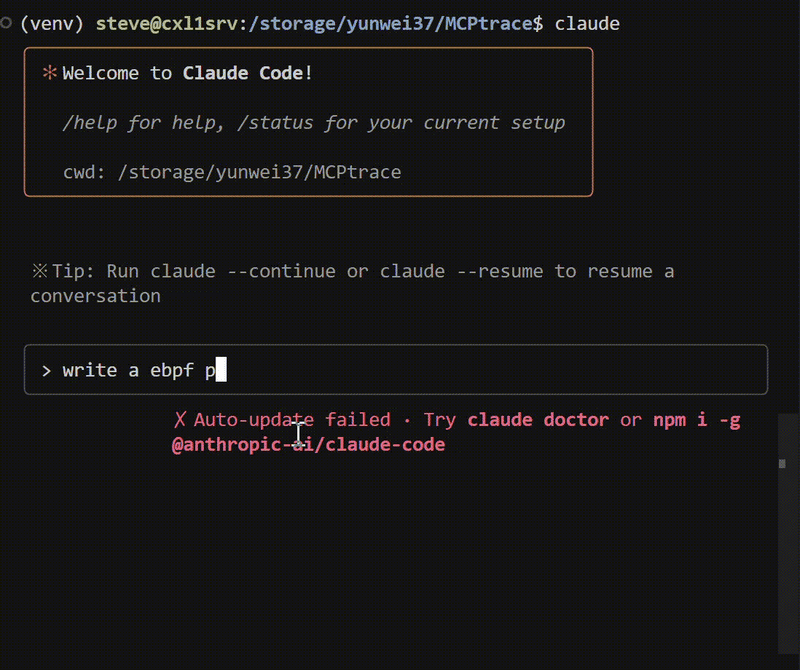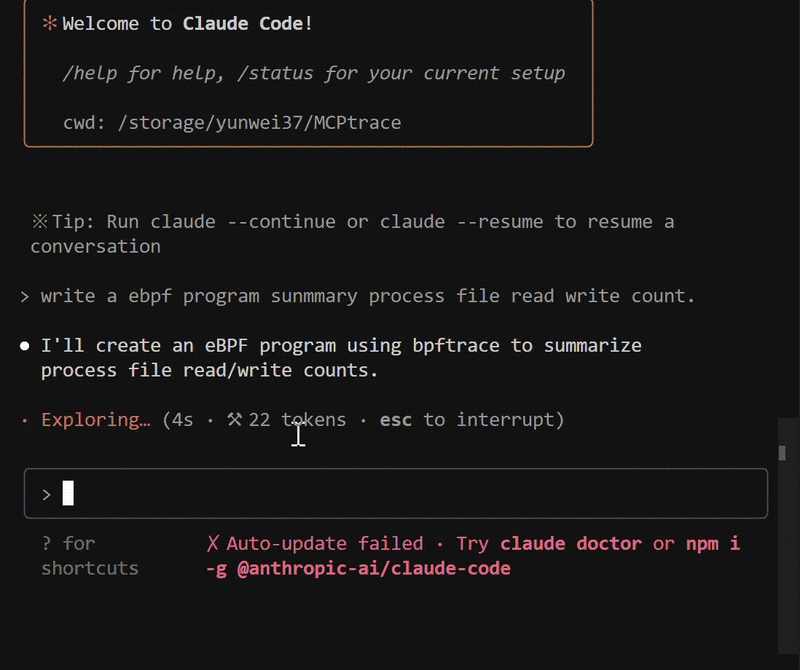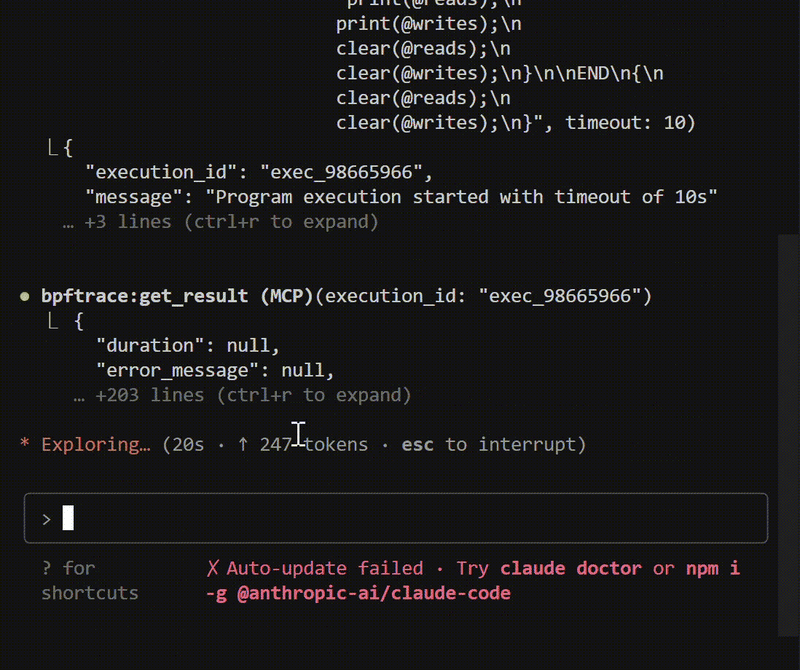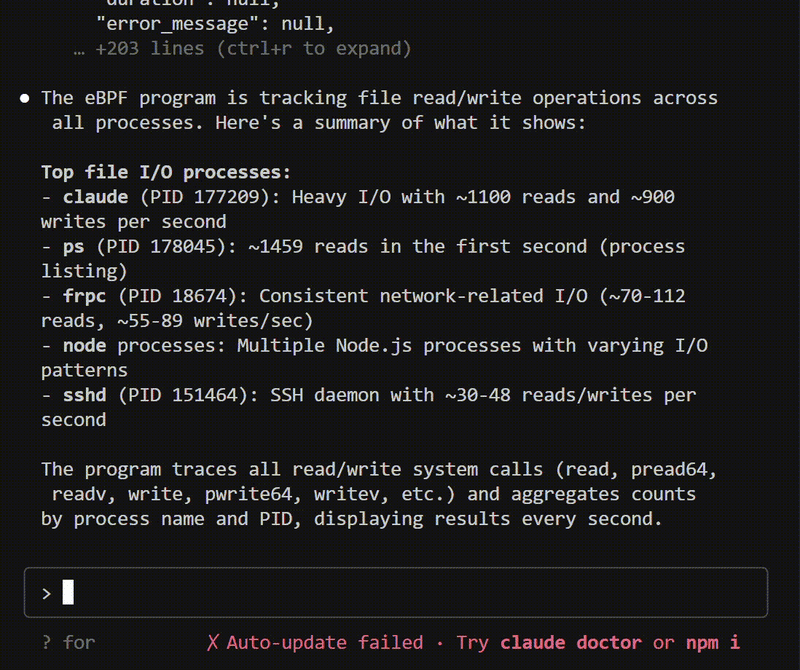
Features
AI-Powered Kernel Debugging: Enable AI assistants to help you debug complex Linux kernel issues through natural language - no eBPF expertise required
Discover System Trace Points: Browse and search through thousands of kernel probes to find exactly what you need to monitor - from system calls to network packets
Rich Context and Examples: Access a curated collection of production-ready bpftrace scripts for common debugging scenarios like performance bottlenecks, security monitoring, and system troubleshooting
Secure Execution Model: Run kernel traces safely without giving AI direct root access - MCPtrace acts as a secure gateway with proper authentication
Asynchronous Operation: Start long-running traces and retrieve results later - perfect for monitoring production issues that occur intermittently
System Capability Detection: Automatically discover what tracing features your kernel supports, including available helpers, map types, and probe types
Related MCP server: Scrapybara MCP
Why MCPtrace?
Debugging kernel issues traditionally requires deep eBPF expertise. MCPtrace changes that.
By bridging AI assistants with bpftrace (the perfect eBPF tracing language), MCPtrace lets you debug complex system issues through natural conversation. Just describe what you want to observe - "show me which processes are opening files" or "trace slow disk operations" - and let AI generate the appropriate kernel traces.
AI never gets root access. MCPtrace acts as a secure gateway, and with its rich collection of example scripts and probe information, AI has everything needed to help you understand what's happening inside your kernel. No eBPF expertise required.
Installation
Prerequisites
Install Rust (if not already installed):
Ensure bpftrace is installed:
Install from crates.io (Recommended)
This will install the bpftrace-mcp-server binary to your Cargo bin directory (usually ~/.cargo/bin/).
Build from Source
Alternatively, you can build from source:
The binary will be available at ./target/release/bpftrace-mcp-server.
Quick Setup
Use our automated setup scripts:
Claude Desktop:
./setup/setup_claude.shClaude Code:
./setup/setup_claude_code.sh
For detailed setup instructions and manual configuration, see setup/SETUP.md.
Running the Server
If installed via cargo install
If built from source
Development mode (from source)
Manual Configuration
For manual setup instructions for Claude Desktop or Claude Code, see setup/SETUP.md.
Usage Examples
List System Call Probes
Get BPF System Information
Execute a Simple Trace
Get Results
Security Notes
The server requires sudo access for bpftrace
Password Handling: Create a
.envfile with your sudo password:echo "BPFTRACE_PASSWD=your_sudo_password" > .envAlternative: Configure passwordless sudo for bpftrace:
sudo visudo # Add: your_username ALL=(ALL) NOPASSWD: /usr/bin/bpftraceNo script validation - trust the AI client to generate safe scripts
Resource limits: 60s max execution, 10k lines buffer
See SECURITY.md for detailed security configuration
Architecture
The Rust server uses:
Tokio async runtime for concurrent operations
Subprocess management for bpftrace execution
DashMap for thread-safe in-memory buffering
Automatic cleanup of old buffers
rmcp crate for MCP protocol implementation
Limitations
No real-time streaming (use get_result to poll)
Simple password handling (improve for production)
No persistent storage of executions
Basic error handling
Documentation
Setup Guide - Detailed installation and configuration
Claude Code Setup - Claude Code specific instructions
CLAUDE.md - Development guidance for AI assistants
Design Document - Architecture and design details
Future Enhancements
Add SSE transport for real-time streaming
Implement proper authentication
Add script validation and sandboxing
Support for saving/loading trace sessions
Integration with eBPF programs