Servidores MCP remotos seguros mediante Azure API Management (experimental)
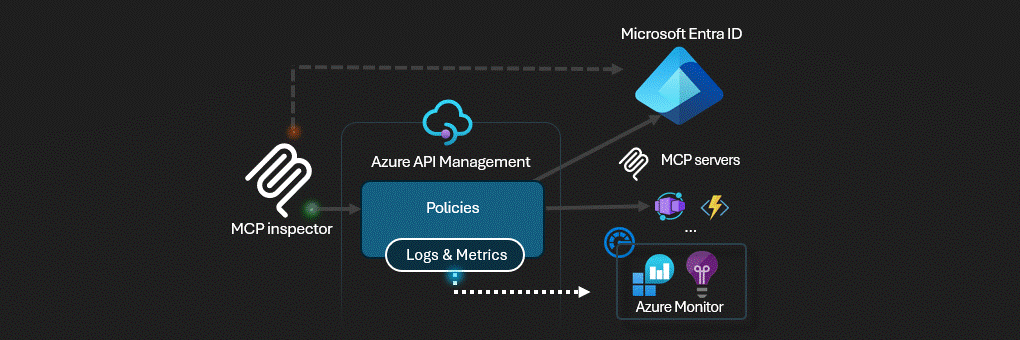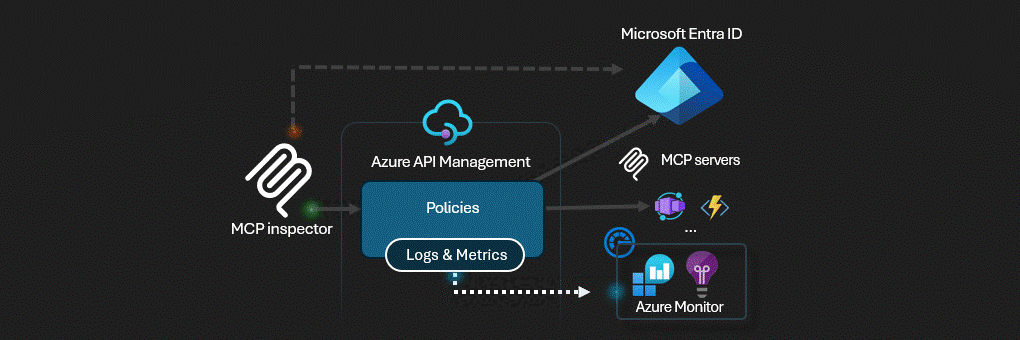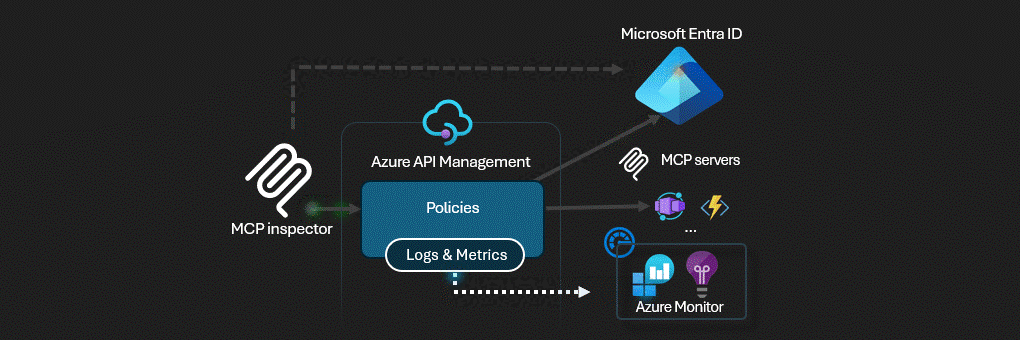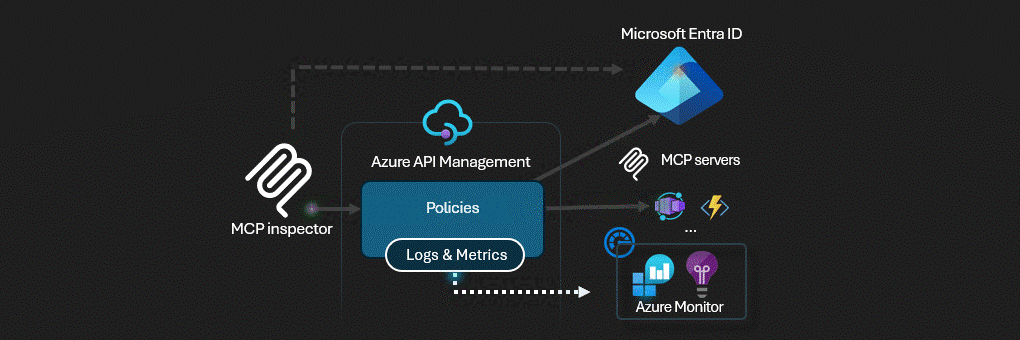
Azure API Management actúa como puerta de enlace de inteligencia artificial para servidores MCP.
Esta muestra implementa la última especificación de autorización MCP
Este es un diagrama de secuencia para entender el flujo.
Implementar un servidor MCP remoto en Azure
Registrar proveedor de recursos
Microsoft.App.Si está utilizando la CLI de Azure, ejecute
az provider register --namespace Microsoft.App --wait.Si usa Azure PowerShell, ejecute
Register-AzResourceProvider -ProviderNamespace Microsoft.App. Después de un tiempo, ejecute(Get-AzResourceProvider -ProviderNamespace Microsoft.App).RegistrationStatepara comprobar si el registro se ha completado.
Ejecute este comando azd para aprovisionar el servicio de administración de API, la aplicación de función (con código) y todos los demás recursos de Azure necesarios
azd up
Inspector de MCP
En una nueva ventana de terminal , instale y ejecute MCP Inspector
npx @modelcontextprotocol/inspectorMantenga presionada la tecla CTRL y haga clic para cargar la aplicación web MCP Inspector desde la URL que muestra la aplicación (por ejemplo, http://127.0.0.1:6274/#resources )
Establezca el tipo de transporte en
SSEEstablezca la URL de su punto final de API Management SSE en ejecución que se muestra después de
azd upy Connect :https://<apim-servicename-from-azd-output>.azure-api.net/mcp/sseLista de herramientas . Haga clic en una herramienta y seleccione Ejecutar herramienta .