Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@Base MCP Servercheck my wallet balance"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
Base MCP Server 🔵
A Model Context Protocol (MCP) server that provides onchain tools for AI applications like Claude Desktop and Cursor, allowing them to interact with the Base Network and Coinbase API.
Overview
This MCP server extends any MCP client's capabilities by providing tools to do anything on Base:
Retrieve wallet addresses
List wallet balances
Transfer funds between wallets
Deploy smart contracts
Interact with Morpho vaults for onchain lending
Call contract functions
Onramp funds via Coinbase
Manage ERC20 tokens
List and transfer NFTs (ERC721 and ERC1155)
Buy OpenRouter credits with USDC
Resolve Farcaster usernames to Ethereum addresses
The server interacts with Base, powered by Base Developer Tools and AgentKit.
Related MCP server: Adamik MCP Server
Extending Base MCP with 3P Protocols, Tools, and Data Sources
Base MCP is designed to be extensible, allowing you to add your own third-party protocols, tools, and data sources. This section provides an overview of how to extend the Base MCP server with new capabilities.
Adding New Tools
If you want to add a new tool to the Base MCP server, follow these steps:
Create a new directory in the
src/toolsdirectory for your toolImplement the tool following the existing patterns:
index.ts: Define and export your tools. Tools are defined as AgentKit ActionProviders.schemas.ts: Define input schemas for your toolstypes.ts: Define types required for your toolsutils.ts: Utilities for your tools
Add your tool to the list of available tools in
src/main.tsAdd documentation for your tool in the README.md
Add examples of how to use your tool in examples.md
Write tests for your tool
Project Structure
The Base MCP server follows this structure for tools:
Best Practices for Tool Development
When developing new tools for Base MCP:
Follow the existing code style and patterns
Ensure your tool has a clear, focused purpose
Provide comprehensive input validation
Include detailed error handling
Write thorough documentation
Add examples demonstrating how to use your tool
Include tests for your tool
For more detailed information on contributing to Base MCP, including adding new tools and protocols, see the CONTRIBUTING.md file.
Prerequisites
Node.js (v16 or higher)
npm or yarn
Coinbase API credentials (API Key Name and Private Key)
A wallet seed phrase
Coinbase Project ID (for onramp functionality)
Alchemy API Key (required for NFT functionality)
Optional: OpenRouter API Key (for buying OpenRouter credits)
Installation
Option 1: Install from npm (Recommended)
Once the package is installed, you can configure clients with the following command:
Option 2: Install from Source
Clone this repository:
git clone https://github.com/base/base-mcp.git cd base-mcpInstall dependencies:
npm installBuild the project:
npm run buildOptionally, link it globally:
npm link
Configuration
Create a .env file with your credentials:
Testing
Test the MCP server to verify it's working correctly:
This script will verify that your MCP server is working correctly by testing the connection and available tools.
Examples
See the examples.md file for detailed examples of how to interact with the Base MCP tools through Claude.
Integration with Claude Desktop
To add this MCP server to Claude Desktop:
Create or edit the Claude Desktop configuration file at:
macOS:
~/Library/Application Support/Claude/claude_desktop_config.jsonWindows:
%APPDATA%\Claude\claude_desktop_config.jsonLinux:
~/.config/Claude/claude_desktop_config.json
You can easily access this file via the Claude Desktop app by navigating to Claude > Settings > Developer > Edit Config.
Add the following configuration:
{ "mcpServers": { "base-mcp": { "command": "npx", "args": ["-y", "base-mcp@latest"], "env": { "COINBASE_API_KEY_NAME": "your_api_key_name", "COINBASE_API_PRIVATE_KEY": "your_private_key", "SEED_PHRASE": "your seed phrase here", "COINBASE_PROJECT_ID": "your_project_id", "ALCHEMY_API_KEY": "your_alchemy_api_key", "PINATA_JWT": "your_pinata_jwt", "OPENROUTER_API_KEY": "your_openrouter_api_key", "CHAIN_ID": "optional_for_base_sepolia_testnet" }, "disabled": false, "autoApprove": [] } } }Restart Claude Desktop for the changes to take effect.
Available Tools
get-address
Retrieves the address for your wallet.
Example query to Claude:
"What's my wallet address?"
list-balances
Lists all balances for your wallet.
Example query to Claude:
"Show me my wallet balances."
transfer-funds
Transfers funds from your wallet to another address.
Parameters:
destination: The address to which to transfer fundsassetId: The asset ID to transferamount: The amount of funds to transfer
Example query to Claude:
"Transfer 0.01 ETH to 0x1234567890abcdef1234567890abcdef12345678."
deploy-contract
Deploys a smart contract to the blockchain.
Parameters:
constructorArgs: The arguments for the contract constructorcontractName: The name of the contract to deploysolidityInputJson: The JSON input for the Solidity compiler containing contract source and settingssolidityVersion: The version of the solidity compiler
Example query to Claude:
"Deploy a simple ERC20 token contract for me."
check-address-reputation
Checks the reputation of an address.
Parameters:
address: The Ethereum address to check
Example query to Claude:
"What's the reputation of 0x1234567890abcdef1234567890abcdef12345678?"
get_morpho_vaults
Gets the vaults for a given asset on Morpho.
Parameters:
assetSymbol: Asset symbol by which to filter vaults (optional)
Example query to Claude:
"Show me the available Morpho vaults for USDC."
call_contract
Calls a contract function on the blockchain.
Parameters:
contractAddress: The address of the contract to callfunctionName: The name of the function to callfunctionArgs: The arguments to pass to the functionabi: The ABI of the contractvalue: The value of ETH to send with the transaction (optional)
Example query to Claude:
"Call the balanceOf function on the contract at 0x1234567890abcdef1234567890abcdef12345678."
get_onramp_assets
Gets the assets available for onramping in a given country/subdivision.
Parameters:
country: ISO 3166-1 two-digit country code string representing the purchasing user's country of residencesubdivision: ISO 3166-2 two-digit country subdivision code (required for US)
Example query to Claude:
"What assets can I onramp in the US, specifically in New York?"
onramp
Gets a URL for onramping funds via Coinbase.
Parameters:
amountUsd: The amount of funds to onrampassetId: The asset ID to onramp
Example query to Claude:
"I want to onramp $100 worth of ETH."
erc20_balance
Gets the balance of an ERC20 token.
Parameters:
contractAddress: The address of the ERC20 contract
Example query to Claude:
"What's my balance of the token at 0x1234567890abcdef1234567890abcdef12345678?"
erc20_transfer
Transfers an ERC20 token to another address.
Parameters:
contractAddress: The address of the ERC20 contracttoAddress: The address of the recipientamount: The amount of tokens to transfer
Example query to Claude:
"Transfer 10 USDC to 0x1234567890abcdef1234567890abcdef12345678."
list_nfts
Lists NFTs owned by a specific address.
Parameters:
ownerAddress: The address of the owner whose NFTs to listlimit: Maximum number of NFTs to return (default: 50)
Example query to Claude:
"Show me the NFTs owned by 0x89A93a48C6Ef8085B9d07e46AaA96DFDeC717040."
transfer_nft
Transfers an NFT to another address. Supports both ERC721 and ERC1155 standards.
Parameters:
contractAddress: The address of the NFT contracttokenId: The token ID of the NFT to transfertoAddress: The address of the recipientamount: The amount to transfer (only used for ERC1155, default: 1)
Example query to Claude:
"Transfer my NFT with contract 0x3F06FcF75f45F1bb61D56D68fA7b3F32763AA15c and token ID 56090175025510453004781233574040052668718235229192064098345825090519343038548 to 0x1234567890abcdef1234567890abcdef12345678."
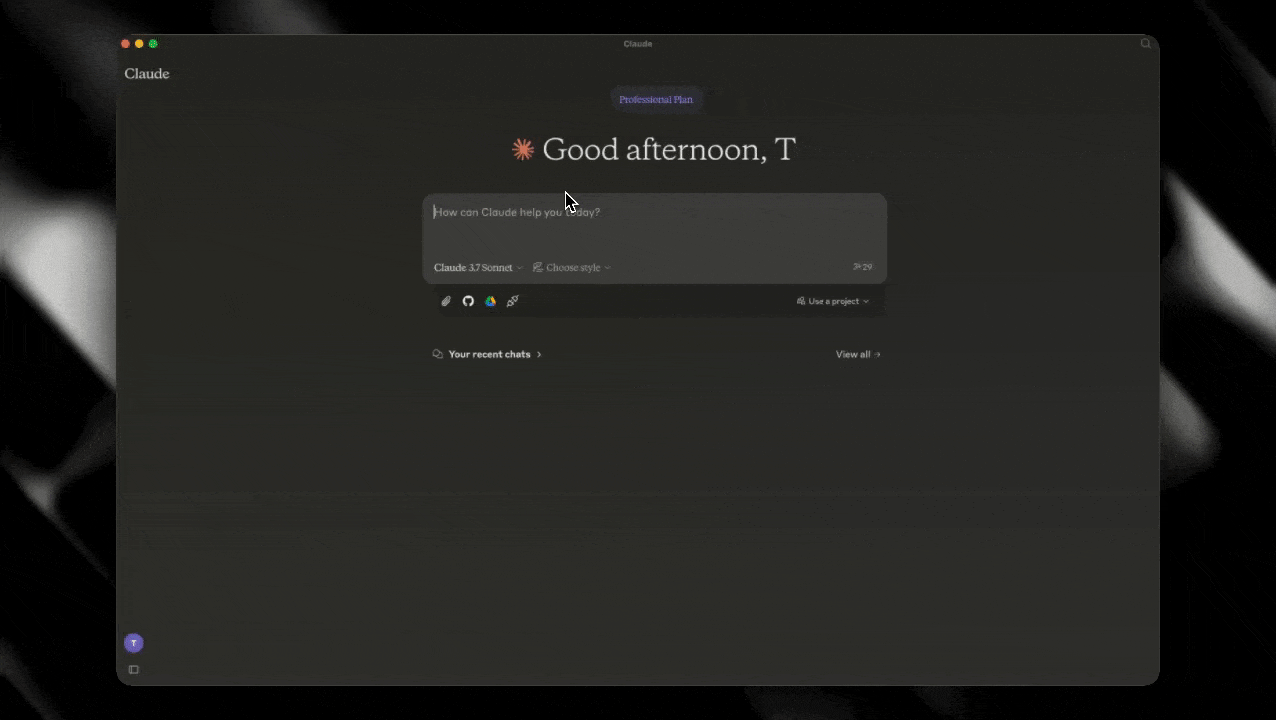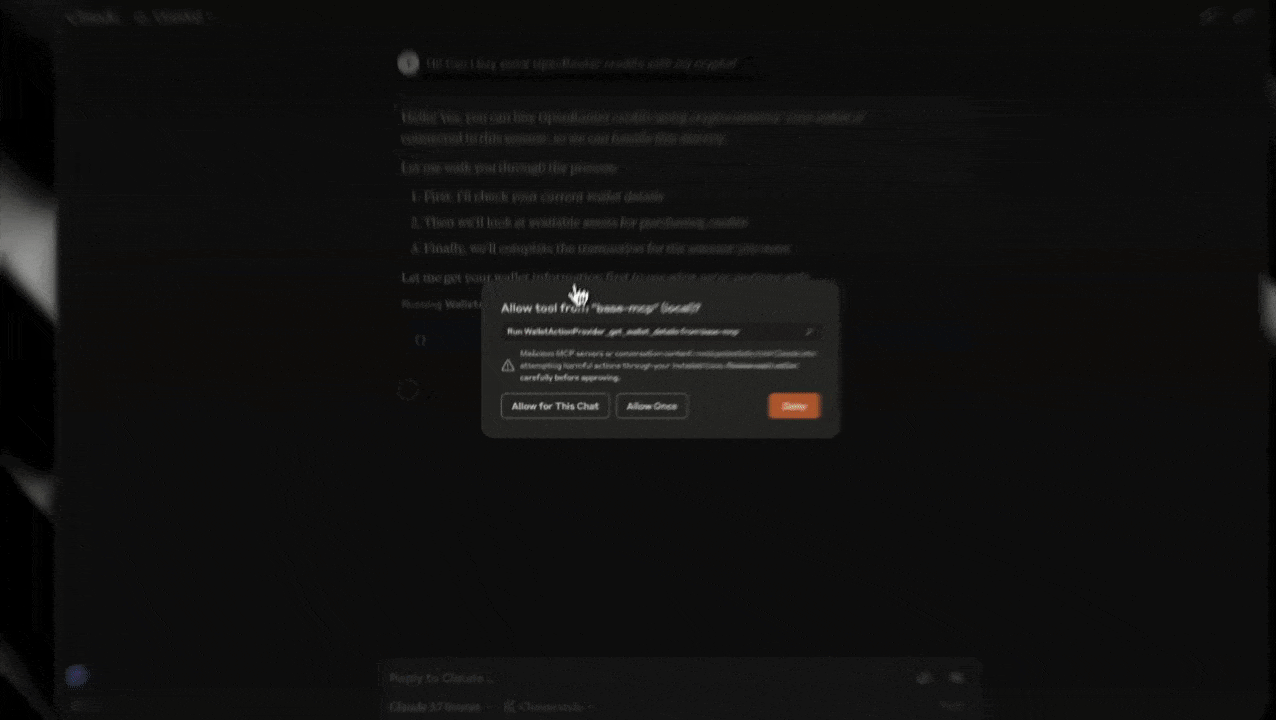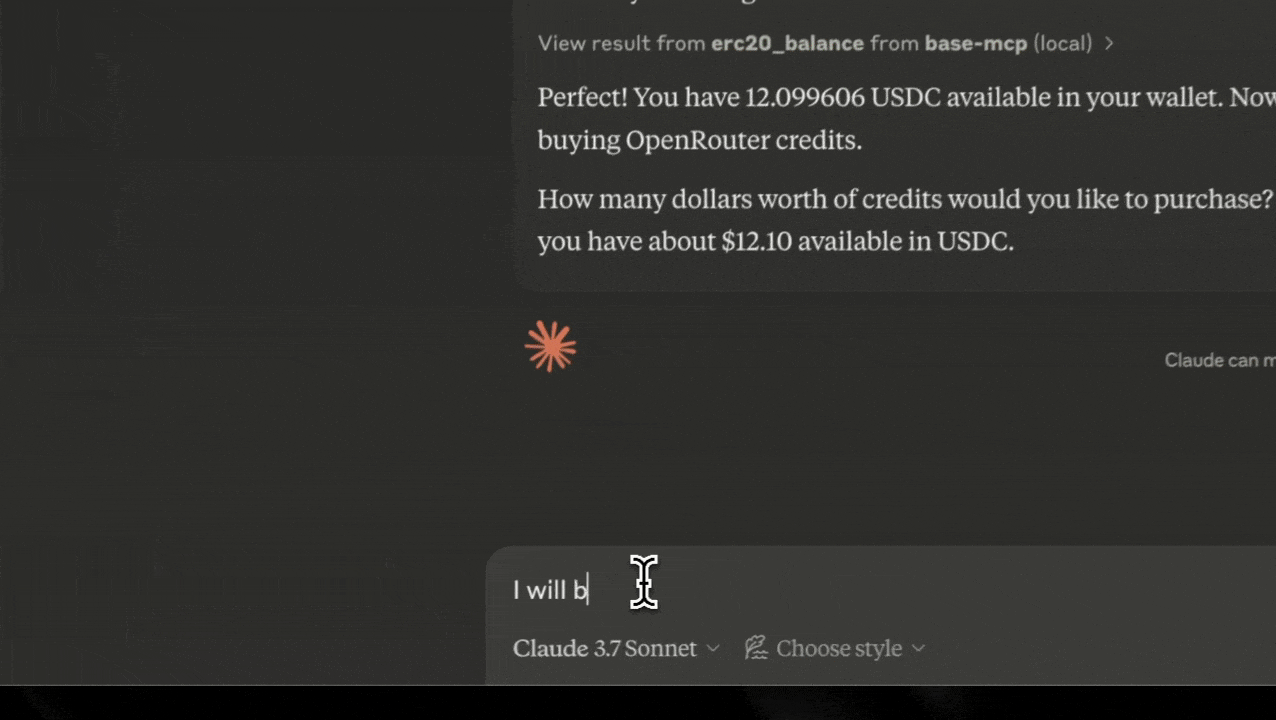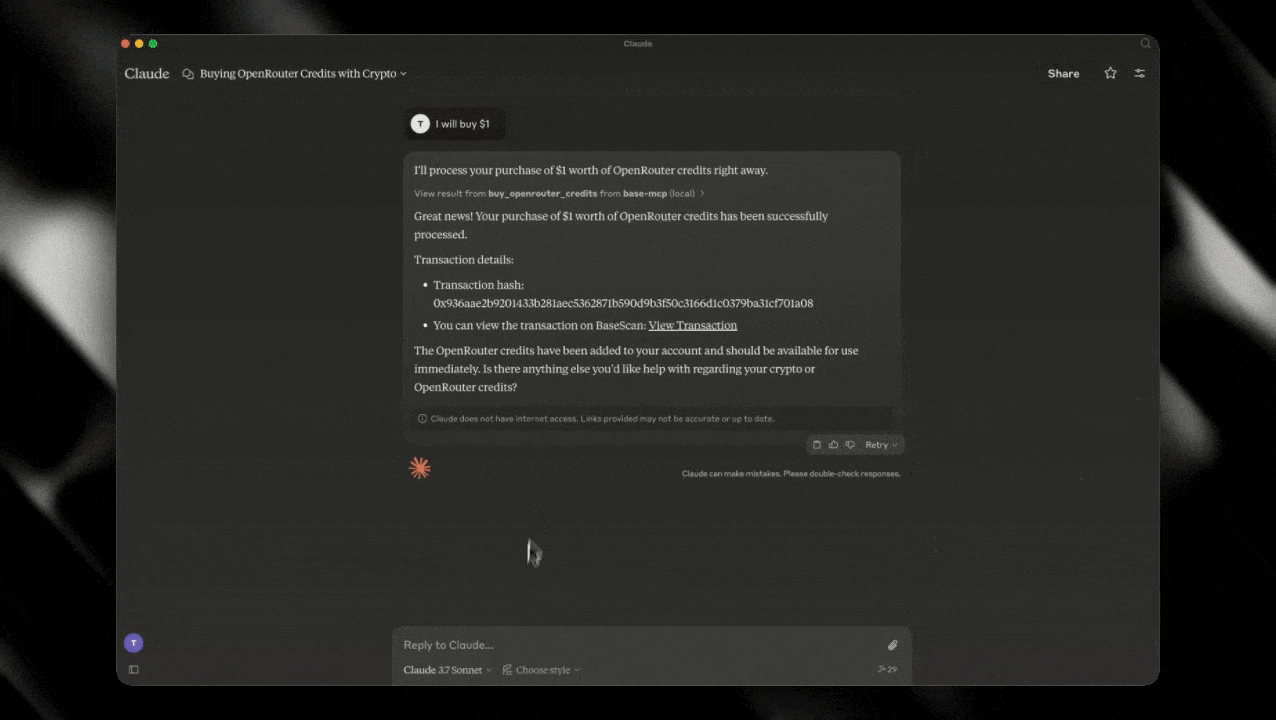
buy_openrouter_credits
Buys OpenRouter credits with USDC.
Parameters:
amountUsd: The amount of credits to buy, in USD
Example query to Claude:
"Buy $20 worth of OpenRouter credits."
Security Considerations
The configuration file contains sensitive information (API keys and seed phrases). Ensure it's properly secured and not shared.
Consider using environment variables or a secure credential manager instead of hardcoding sensitive information.
Be cautious when transferring funds or deploying contracts, as these operations are irreversible on the blockchain.
When using the onramp functionality, ensure you're on a secure connection.
Verify all transaction details before confirming, especially when transferring funds or buying credits.
Troubleshooting
If you encounter issues:
Check that your Coinbase API credentials are correct
Verify that your seed phrase is valid
Ensure you're on the correct network (Base Mainnet)
Check the Claude Desktop logs for any error messages
License
Contributing
Contributions are welcome! Please feel free to submit a Pull Request.
For detailed guidelines on contributing to Base MCP, including:
Reporting bugs
Suggesting enhancements
Development setup
Coding standards
Adding new tools, protocols, and data sources (see also the Extending Base MCP section above)
Testing requirements
Documentation standards
Please refer to our comprehensive CONTRIBUTING.md guide.
Basic contribution steps:
Fork the repository
Create your feature branch (
git checkout -b feature/amazing-feature)Commit your changes (
git commit -m 'Add some amazing feature')Push to the branch (
git push origin feature/amazing-feature)Open a Pull Request
Please make sure your code follows the existing style and includes appropriate tests.