The BloodHound MCP server enables natural language interaction with Active Directory and Azure Active Directory environments using Large Language Models, allowing for complex queries and analysis without manual Cypher scripting.
Capabilities include:
Natural Language Queries: Perform AD/AAD queries using conversational commands
Execute Raw Cypher database queries
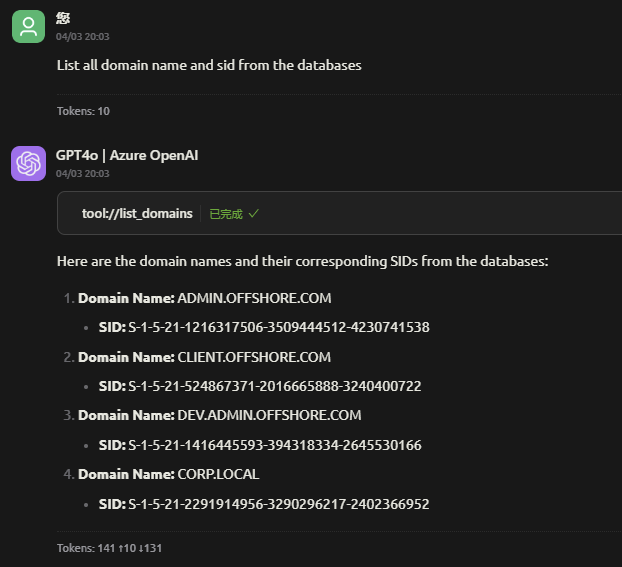
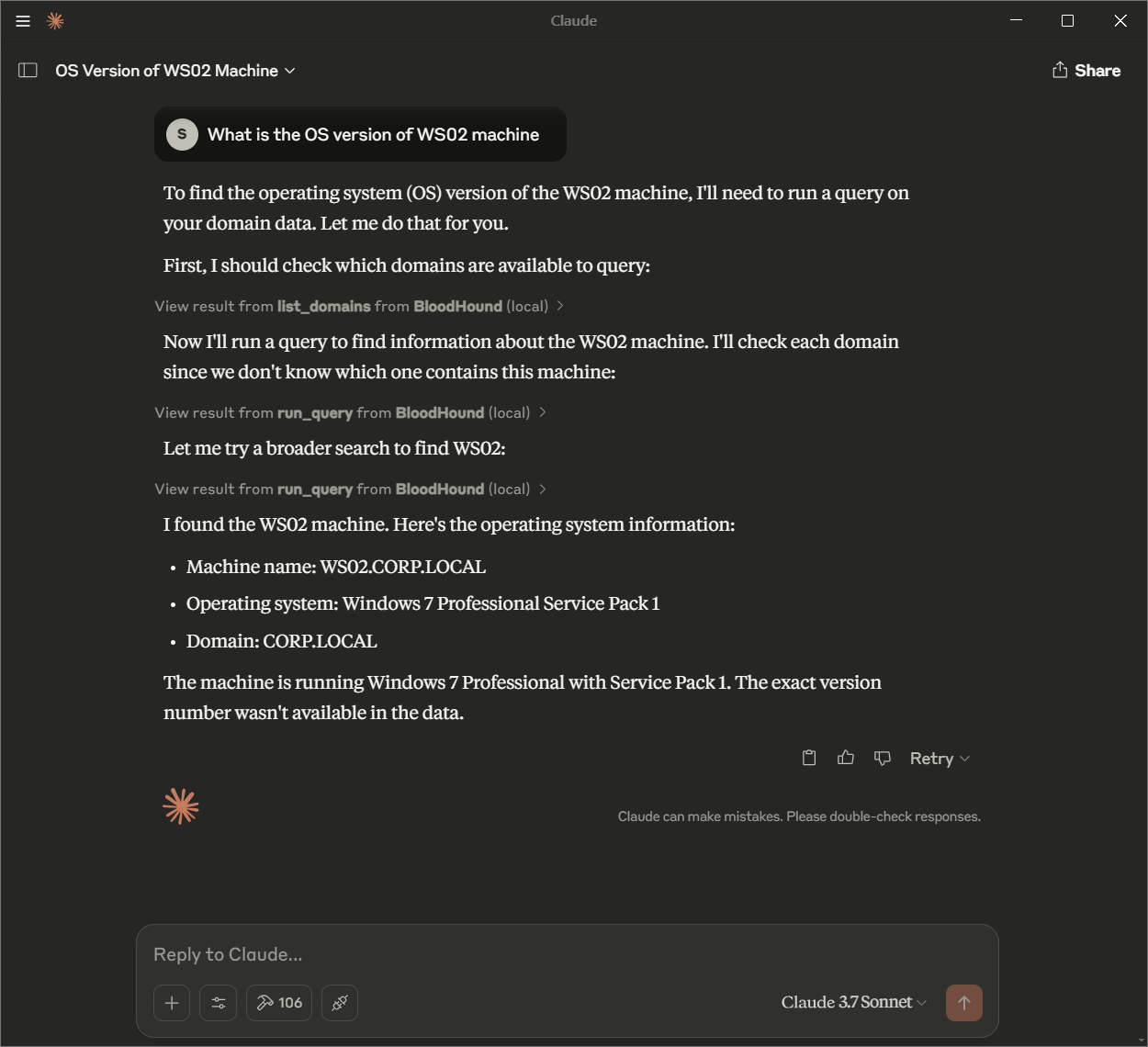
List AD Objects: Query users, computers, groups, domains, trusts, GPOs, network shares, and certificate templates based on various attributes
Identify Vulnerabilities: Find users vulnerable to AS-REP roasting, Kerberoasting, or with dangerous rights
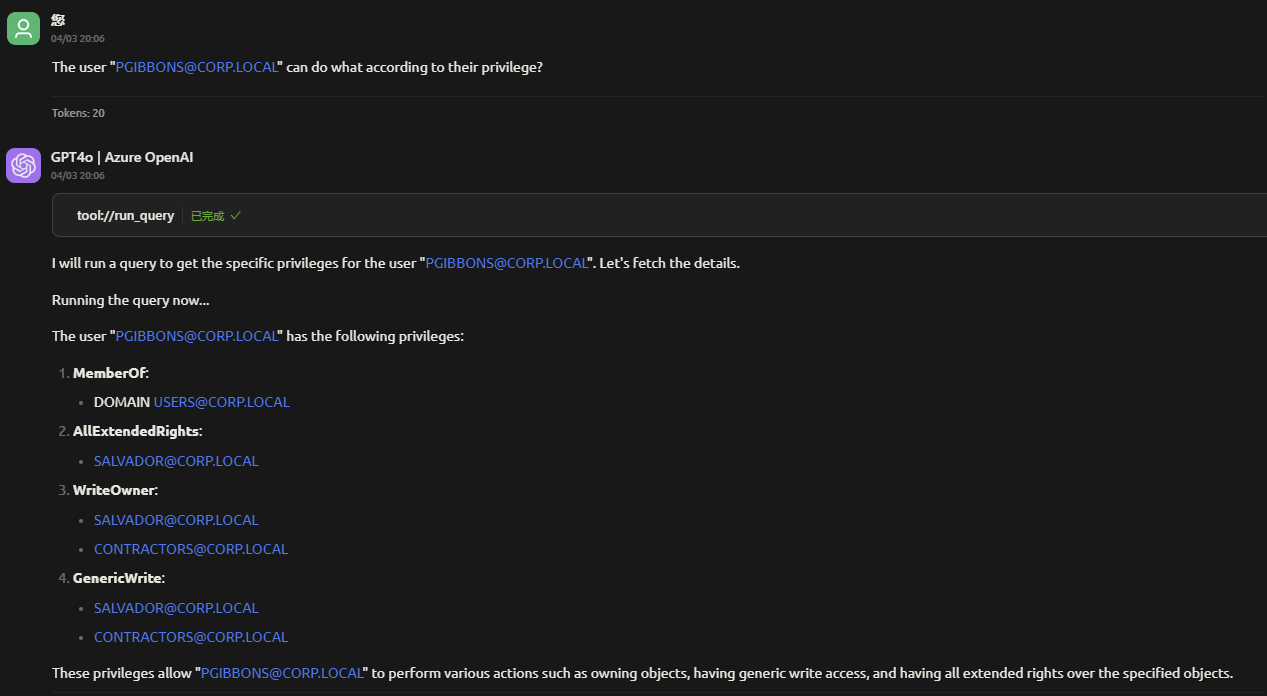
Security Analysis: Identify privileged users, dangerous permissions, high-value targets, and vulnerable certificate templates (ESC1-ESC8)
Attack Path Routing: Map paths between objects based on permissions, sessions, or relationships
Azure Integration: Analyze Azure environments, list AAD groups synchronized with AD, and find paths to Azure VMs or Global Administrators (requires AzureHound)
Session Analysis: List and route based on active user sessions (requires sessions data)
Integrates with Neo4j database to store and query BloodHound data about Active Directory and Azure Active Directory environments, enabling natural language queries for security analysis without writing Cypher queries directly.
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@BloodHound MCPshow me all users with admin privileges in the domain"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
BloodHound MCP
BloodHound MCP (Model Context Protocol) is an innovative extension of the BloodHound tool, designed to enable Large Language Models (LLMs) to interact with and analyze Active Directory (AD) and Azure Active Directory (AAD) environments through natural language queries. By leveraging the power of LLMs, BloodHound MCP allows users to perform complex queries and retrieve insights from their AD/AAD environments using simple, conversational commands.
Features
Natural Language Queries: Use conversational language to query your AD/AAD environment without needing to write Cypher queries manually.
LLM-Powered Analysis: Harness the capabilities of Large Language Models to interpret and execute queries on your behalf.
Seamless Integration: Works with existing BloodHound data stored in Neo4j, providing a user-friendly interface for complex analysis.
Customizable: Easily configure the system to work with your specific environment and tools.
Related MCP server: File Context MCP
Configure the MCP Server
Usage
Configuration
To customize BloodHound MCP, update the configuration file in your MCP-supported tool. Key settings include:
Neo4j Database Connection:
BLOODHOUND_URI: The URI of your Neo4j database (e.g., bolt://localhost:7687).BLOODHOUND_USERNAME: Your Neo4j username.BLOODHOUND_PASSWORD: Your Neo4j password.
Server Settings: Adjust the command and args to match your environment and tool requirements.
Contributing
We welcome contributions to BloodHound MCP! To get involved:
Fork the Repository: Create your own copy on GitHub.
Create a Branch: Work on your feature or fix in a new branch.
Submit a Pull Request: Include a clear description of your changes.
Special Thanks
Custom queries from : https://github.com/CompassSecurity/BloodHoundQueries
Tools
- computers_with_most_sessions
- find_all_enabled_as_rep_roastable_users
- find_all_enabled_kerberoastable_users
- find_all_owned_groups_granting_network_share_access
- find_allshortestpaths_with_dcsync_to_domain
- find_allshortestpaths_with_shadow_credential_permission
- find_azure_app_owners_with_dangerous_rights
- find_enabled_certificate_templates