This server allows you to interact with cryptocurrency exchanges through various functionalities:
Market Data: Access real-time tickers, order books, OHLCV charts, recent trades, and available markets
Trading Operations: Execute market orders, place futures orders, and set trading parameters
Account Management: View balances and trading configurations
Exchange Information: List available exchanges, view exchange details, supported market types, leverage tiers, and funding rates
Configuration Options: Set leverage, margin modes, default market types, and proxy settings
Cache Management: Get statistics and clear CCXT cache
Logging: Configure logging levels for debugging
Enables reverse engineering capabilities with IRIS Reverse Engineering technology, referenced as a related project (MxIris-Reverse-Engineering).
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@PCMdecompile the function at 0x401000"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
pcm
PCM (MCP but reversed), MCP for reverse engineering.
Features
Analysis
IDA
repl (IDAPython)
disassembly
decompilation
set types
...
Memory
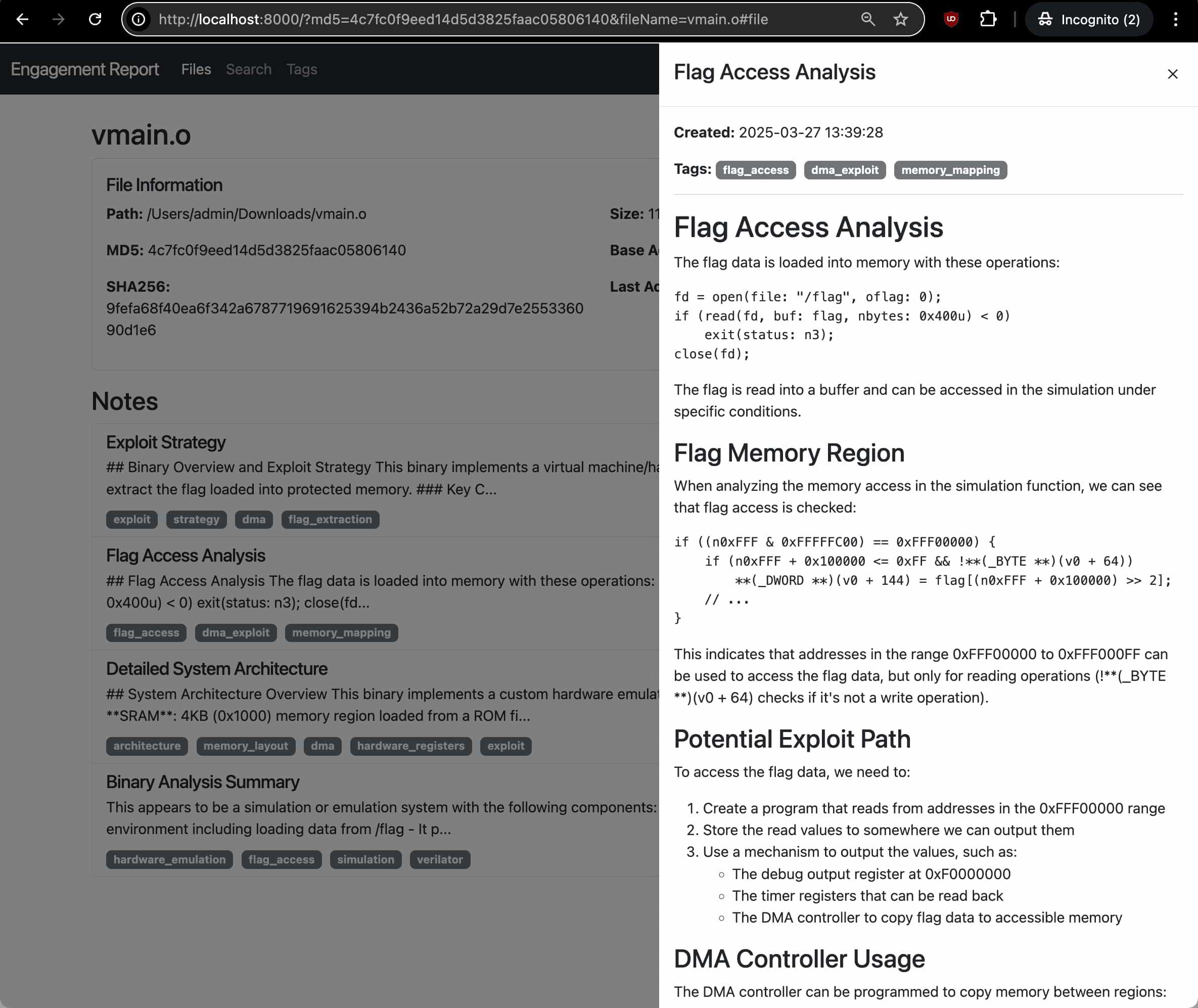
Engagement reports
Related MCP server: IDA Pro MCP
Installations
Prerequisites:
Clone the repository
git clone https://github.com/rand-tech/pcmAdd
pcmto you mcp config example{ "mcpServers": { "pcm": { "command": "uv", "args": [ "--directory", "path_to/pcm", "run", "server.py" ] } } }Use the MCP
Related projects:
Attribution: This project is based on IDA Pro MCP by Duncan Ogilvie (@mrexodia). Thank you
License: This project is licensed under the MIT License - see the LICENSE file for details. The original code is also licensed under the MIT License.