The Slack MCP server allows integration with Slack Workspaces to fetch channel information and message history without requiring admin permissions or bots. It supports:
Fetching channel lists (
channels_list):Filter by channel types ('mpim', 'im', 'public_channel', 'private_channel')
Sort by popularity (number of members/participants)
Retrieving message history (
conversations_history):Fetch messages from a specific channel using channel_id
Support for pagination with cursors
Limit by number of messages or time range
The server supports both Stdio and SSE transport modes, proxy settings, and secure token-based authentication.
Mentioned as an option for exposing the MCP server to the internet with TLS encryption for the SSE transport method.
Allows interaction with Slack Workspaces, providing tools to retrieve channel histories and list available channels without requiring admin permissions or bot approvals.
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@Slack MCPshow me the last 10 messages from #general"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
Slack MCP Server
Model Context Protocol (MCP) server for Slack Workspaces. The most powerful MCP Slack server — supports Stdio, SSE and HTTP transports, proxy settings, DMs, Group DMs, Smart History fetch (by date or count), may work via OAuth or in complete stealth mode with no permissions and scopes in Workspace 😏.
We need your support! Each month, over 30,000 engineers visit this repository, and more than 9,000 are already using it.
If you appreciate the work our contributors have put into this project, please consider giving the repository a star.
This feature-rich Slack MCP Server has:
Stealth and OAuth Modes: Run the server without requiring additional permissions or bot installations (stealth mode), or use secure OAuth tokens for access without needing to refresh or extract tokens from the browser (OAuth mode).
Enterprise Workspaces Support: Possibility to integrate with Enterprise Slack setups.
Channel and Thread Support with : Fetch messages from channels and threads, including activity messages, and retrieve channels using their names (e.g., #general) as well as their IDs.
Smart History: Fetch messages with pagination by date (d1, 7d, 1m) or message count.
Search Messages: Search messages in channels, threads, and DMs using various filters like date, user, and content.
Safe Message Posting: The
conversations_add_messagetool is disabled by default for safety. Enable it via an environment variable, with optional channel restrictions.DM and Group DM support: Retrieve direct messages and group direct messages.
Embedded user information: Embed user information in messages, for better context.
Cache support: Cache users and channels for faster access.
Stdio/SSE/HTTP Transports & Proxy Support: Use the server with any MCP client that supports Stdio, SSE or HTTP transports, and configure it to route outgoing requests through a proxy if needed.
Analytics Demo
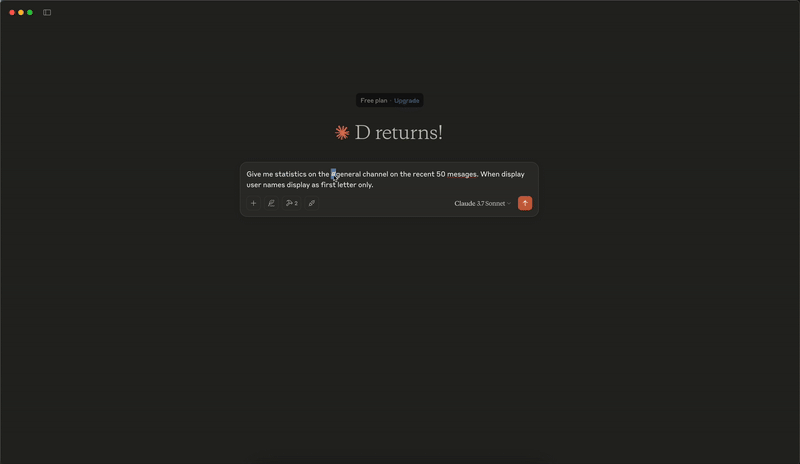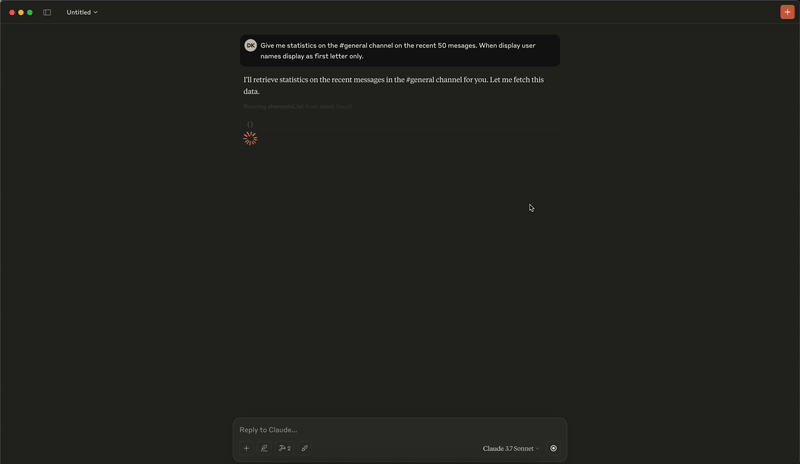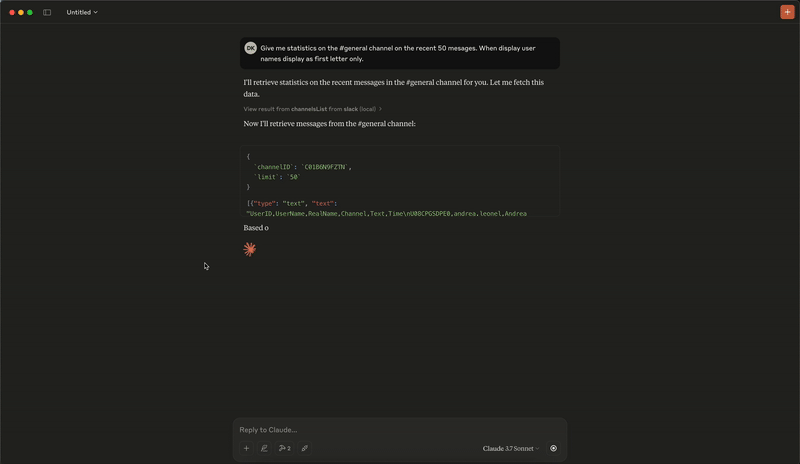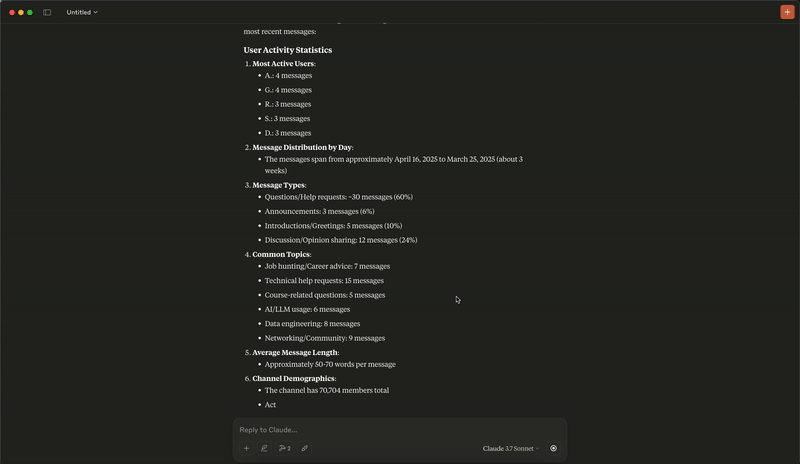
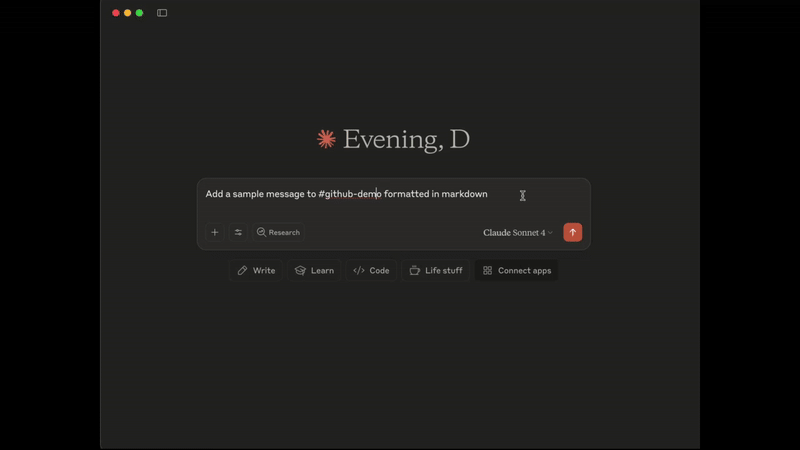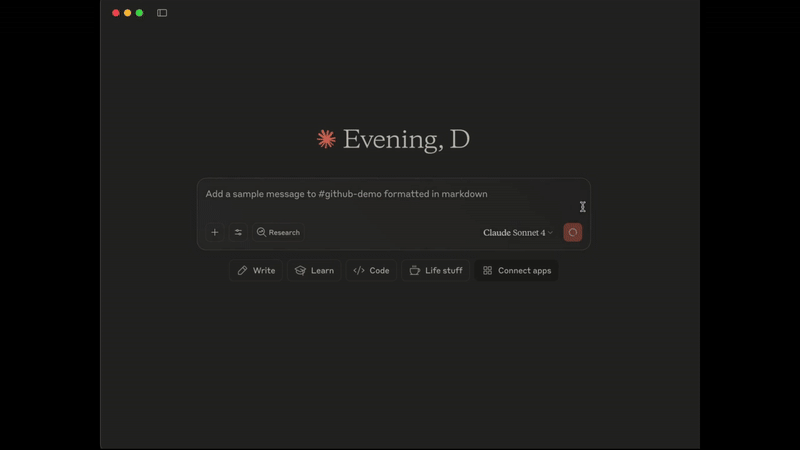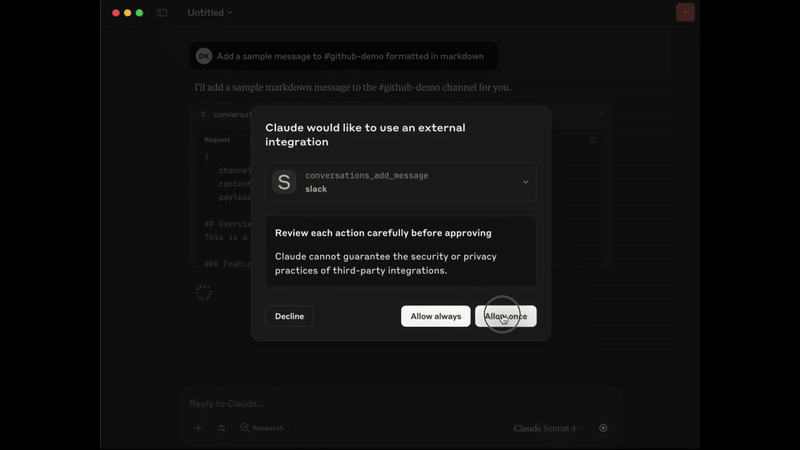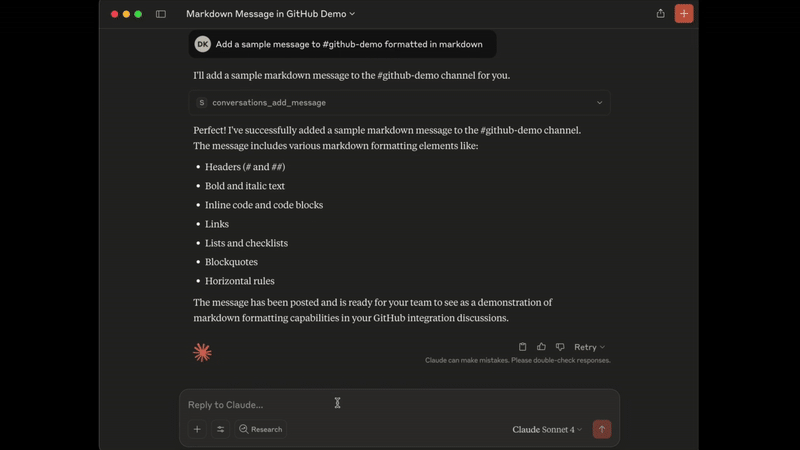
Add Message Demo
Tools
1. conversations_history:
Get messages from the channel (or DM) by channel_id, the last row/column in the response is used as 'cursor' parameter for pagination if not empty
Parameters:
channel_id(string, required): -channel_id(string): ID of the channel in format Cxxxxxxxxxx or its name starting with#...or@...aka#generalor@username_dm.include_activity_messages(boolean, default: false): If true, the response will include activity messages such aschannel_joinorchannel_leave. Default is boolean false.cursor(string, optional): Cursor for pagination. Use the value of the last row and column in the response as next_cursor field returned from the previous request.limit(string, default: "1d"): Limit of messages to fetch in format of maximum ranges of time (e.g. 1d - 1 day, 1w - 1 week, 30d - 30 days, 90d - 90 days which is a default limit for free tier history) or number of messages (e.g. 50). Must be empty when 'cursor' is provided.
2. conversations_replies:
Get a thread of messages posted to a conversation by channelID and thread_ts, the last row/column in the response is used as cursor parameter for pagination if not empty.
Parameters:
channel_id(string, required): ID of the channel in formatCxxxxxxxxxxor its name starting with#...or@...aka#generalor@username_dm.thread_ts(string, required): Unique identifier of either a thread’s parent message or a message in the thread. ts must be the timestamp in format1234567890.123456of an existing message with 0 or more replies.include_activity_messages(boolean, default: false): If true, the response will include activity messages such as 'channel_join' or 'channel_leave'. Default is boolean false.cursor(string, optional): Cursor for pagination. Use the value of the last row and column in the response as next_cursor field returned from the previous request.limit(string, default: "1d"): Limit of messages to fetch in format of maximum ranges of time (e.g. 1d - 1 day, 1w - 1 week, 30d - 30 days, 90d - 90 days which is a default limit for free tier history) or number of messages (e.g. 50). Must be empty when 'cursor' is provided.
3. conversations_add_message
Add a message to a public channel, private channel, or direct message (DM, or IM) conversation by channel_id and thread_ts.
Note: Posting messages is disabled by default for safety. To enable, set the
SLACK_MCP_ADD_MESSAGE_TOOLenvironment variable. If set to a comma-separated list of channel IDs, posting is enabled only for those specific channels. See the Environment Variables section below for details.
Parameters:
channel_id(string, required): ID of the channel in formatCxxxxxxxxxxor its name starting with#...or@...aka#generalor@username_dm.thread_ts(string, optional): Unique identifier of either a thread’s parent message or a message in the thread_ts must be the timestamp in format1234567890.123456of an existing message with 0 or more replies. Optional, if not provided the message will be added to the channel itself, otherwise it will be added to the thread.payload(string, required): Message payload in specified content_type format. Example: 'Hello, world!' for text/plain or '# Hello, world!' for text/markdown.content_type(string, default: "text/markdown"): Content type of the message. Default is 'text/markdown'. Allowed values: 'text/markdown', 'text/plain'.
4. conversations_search_messages
Search messages in a public channel, private channel, or direct message (DM, or IM) conversation using filters. All filters are optional, if not provided then search_query is required.
Note: This tool is not available when using bot tokens (
xoxb-*). Bot tokens cannot use thesearch.messagesAPI.
Parameters:
search_query(string, optional): Search query to filter messages. Example: 'marketing report' or full URL of Slack message e.g. 'https://slack.com/archives/C1234567890/p1234567890123456', then the tool will return a single message matching given URL, herewith all other parameters will be ignored.filter_in_channel(string, optional): Filter messages in a specific channel by its ID or name. Example:C1234567890or#general. If not provided, all channels will be searched.filter_in_im_or_mpim(string, optional): Filter messages in a direct message (DM) or multi-person direct message (MPIM) conversation by its ID or name. Example:D1234567890or@username_dm. If not provided, all DMs and MPIMs will be searched.filter_users_with(string, optional): Filter messages with a specific user by their ID or display name in threads and DMs. Example:U1234567890or@username. If not provided, all threads and DMs will be searched.filter_users_from(string, optional): Filter messages from a specific user by their ID or display name. Example:U1234567890or@username. If not provided, all users will be searched.filter_date_before(string, optional): Filter messages sent before a specific date in formatYYYY-MM-DD. Example:2023-10-01,July,YesterdayorToday. If not provided, all dates will be searched.filter_date_after(string, optional): Filter messages sent after a specific date in formatYYYY-MM-DD. Example:2023-10-01,July,YesterdayorToday. If not provided, all dates will be searched.filter_date_on(string, optional): Filter messages sent on a specific date in formatYYYY-MM-DD. Example:2023-10-01,July,YesterdayorToday. If not provided, all dates will be searched.filter_date_during(string, optional): Filter messages sent during a specific period in formatYYYY-MM-DD. Example:July,YesterdayorToday. If not provided, all dates will be searched.filter_threads_only(boolean, default: false): If true, the response will include only messages from threads. Default is boolean false.cursor(string, default: ""): Cursor for pagination. Use the value of the last row and column in the response as next_cursor field returned from the previous request.limit(number, default: 20): The maximum number of items to return. Must be an integer between 1 and 100.
5. channels_list:
Get list of channels
Parameters:
channel_types(string, required): Comma-separated channel types. Allowed values:mpim,im,public_channel,private_channel. Example:public_channel,private_channel,imsort(string, optional): Type of sorting. Allowed values:popularity- sort by number of members/participants in each channel.limit(number, default: 100): The maximum number of items to return. Must be an integer between 1 and 1000 (maximum 999).cursor(string, optional): Cursor for pagination. Use the value of the last row and column in the response as next_cursor field returned from the previous request.
Related MCP server: Slack Search MCP Server
Resources
The Slack MCP Server exposes two special directory resources for easy access to workspace metadata:
1. slack://<workspace>/channels — Directory of Channels
Fetches a CSV directory of all channels in the workspace, including public channels, private channels, DMs, and group DMs.
URI:
slack://<workspace>/channelsFormat:
text/csvFields:
id: Channel ID (e.g.,C1234567890)name: Channel name (e.g.,#general,@username_dm)topic: Channel topic (if any)purpose: Channel purpose/descriptionmemberCount: Number of members in the channel
2. slack://<workspace>/users — Directory of Users
Fetches a CSV directory of all users in the workspace.
URI:
slack://<workspace>/usersFormat:
text/csvFields:
userID: User ID (e.g.,U1234567890)userName: Slack username (e.g.,john)realName: User’s real name (e.g.,John Doe)
Setup Guide
Environment Variables (Quick Reference)
Variable | Required? | Default | Description |
| Yes* |
| Slack browser token ( |
| Yes* |
| Slack browser cookie |
| Yes* |
| User OAuth token ( |
| Yes* |
| Bot token ( |
| No |
| Port for the MCP server to listen on |
| No |
| Host for the MCP server to listen on |
| No |
| Bearer token for SSE and HTTP transports |
| No |
| Proxy URL for outgoing requests |
| No |
| Custom User-Agent (for Enterprise Slack environments) |
| No |
| Send custom TLS-handshake to Slack servers based on |
| No |
| Path to CA certificate |
| No |
| Inject HTTPToolkit CA certificate to root trust-store for MitM debugging |
| No |
| Trust all insecure requests (NOT RECOMMENDED) |
| No |
| Enable message posting via |
| No |
| When the |
| No |
| Enable to let Slack unfurl posted links or set comma-separated list of domains e.g. |
| No |
| Path to the users cache file. Used to cache Slack user information to avoid repeated API calls on startup. |
| No |
| Path to the channels cache file. Used to cache Slack channel information to avoid repeated API calls on startup. |
| No |
| Log-level for stdout or stderr. Valid values are: |
*You need one of: xoxp (user), xoxb (bot), or both xoxc/xoxd tokens for authentication.
Limitations matrix & Cache
Users Cache | Channels Cache | Limitations |
:x: | :x: | No cache, No LLM context enhancement with user data, tool |
:white_check_mark: | :x: | No channels cache, tool |
:white_check_mark: | :white_check_mark: | No limitations, fully functional Slack MCP Server. |
Debugging Tools
Security
Never share API tokens
Keep .env files secure and private
License
Licensed under MIT - see LICENSE file. This is not an official Slack product.