The MCP SSH Agent server enables AI-powered SSH operations through a standardized interface, leveraging native SSH tools and existing configurations.
Key capabilities:
List known SSH hosts - Get consolidated list of configured hosts, prioritizing
~/.ssh/configentries and including~/.ssh/known_hostsExecute remote commands - Run single shell commands or sequential command batches on remote hosts
File transfers - Upload and download files using
scpbetween local and remote systemsHost management - Retrieve detailed configuration settings and test SSH connectivity
The server provides comprehensive SSH connection management with seamless integration into existing SSH configurations.
Allows executing SSH commands on remote Git repositories, enabling operations like cloning, pushing, pulling, and managing remote Git repositories through secure SSH connections.
Provides SSH connectivity to remote Node.js servers, allowing for deployment, configuration, and management of Node.js applications on remote hosts.
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@MCP SSH Agentlist all my SSH hosts"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
MCP SSH Agent
A Model Context Protocol (MCP) server for managing and controlling SSH connections. This server integrates seamlessly with Claude Desktop and other MCP-compatible clients to provide AI-powered SSH operations.
Overview
This MCP server provides SSH operations through a clean, standardized interface that can be used by MCP-compatible language models like Claude Desktop. The server automatically discovers SSH hosts from your ~/.ssh/config and ~/.ssh/known_hosts files and executes commands using native SSH tools for maximum reliability.
Related MCP server: SSH MCP Server
Quick Start
Desktop Extension Installation (Recommended)
The easiest way to install MCP SSH Agent is through the Desktop Extension (.dxt) format:
Download the latest
mcp-ssh-*.dxtfile from the GitHub releases pageDouble-click the
.dxtfile to install it in Claude DesktopThe SSH tools will be automatically available in your conversations with Claude
Alternative Installation Methods
Installation via npx
Manual Claude Desktop Configuration
To use this MCP server with Claude Desktop using manual configuration, add the following to your MCP settings file:
On macOS: ~/Library/Application Support/Claude/claude_desktop_config.json
On Windows: %APPDATA%/Claude/claude_desktop_config.json
After adding this configuration, restart Claude Desktop. The SSH tools will be available for use in your conversations with Claude.
Global Installation
Local Development
Example Usage
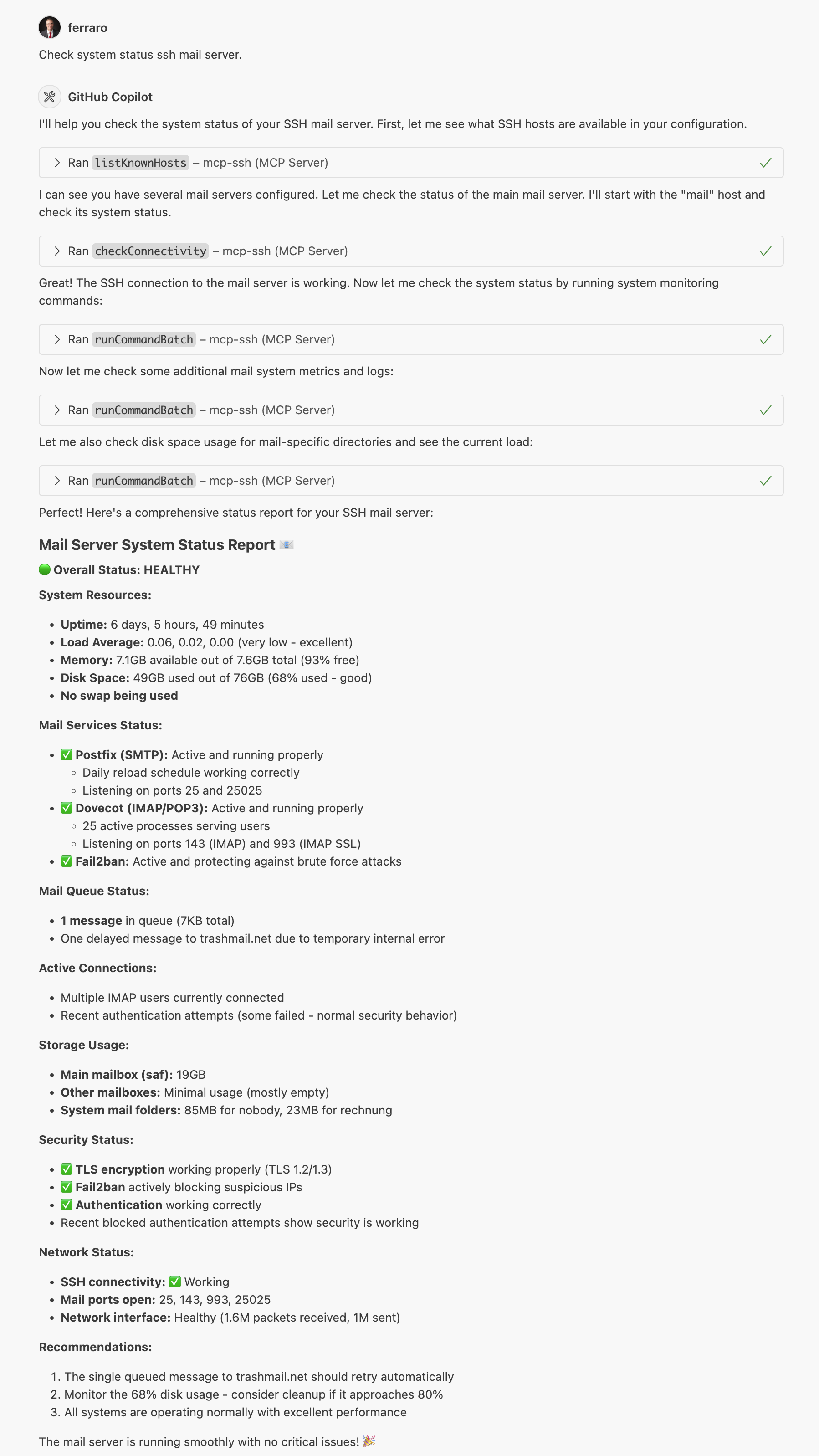
The screenshot above shows the MCP SSH Agent in action, demonstrating how it integrates with MCP-compatible clients to provide seamless SSH operations.
Integration with Claude
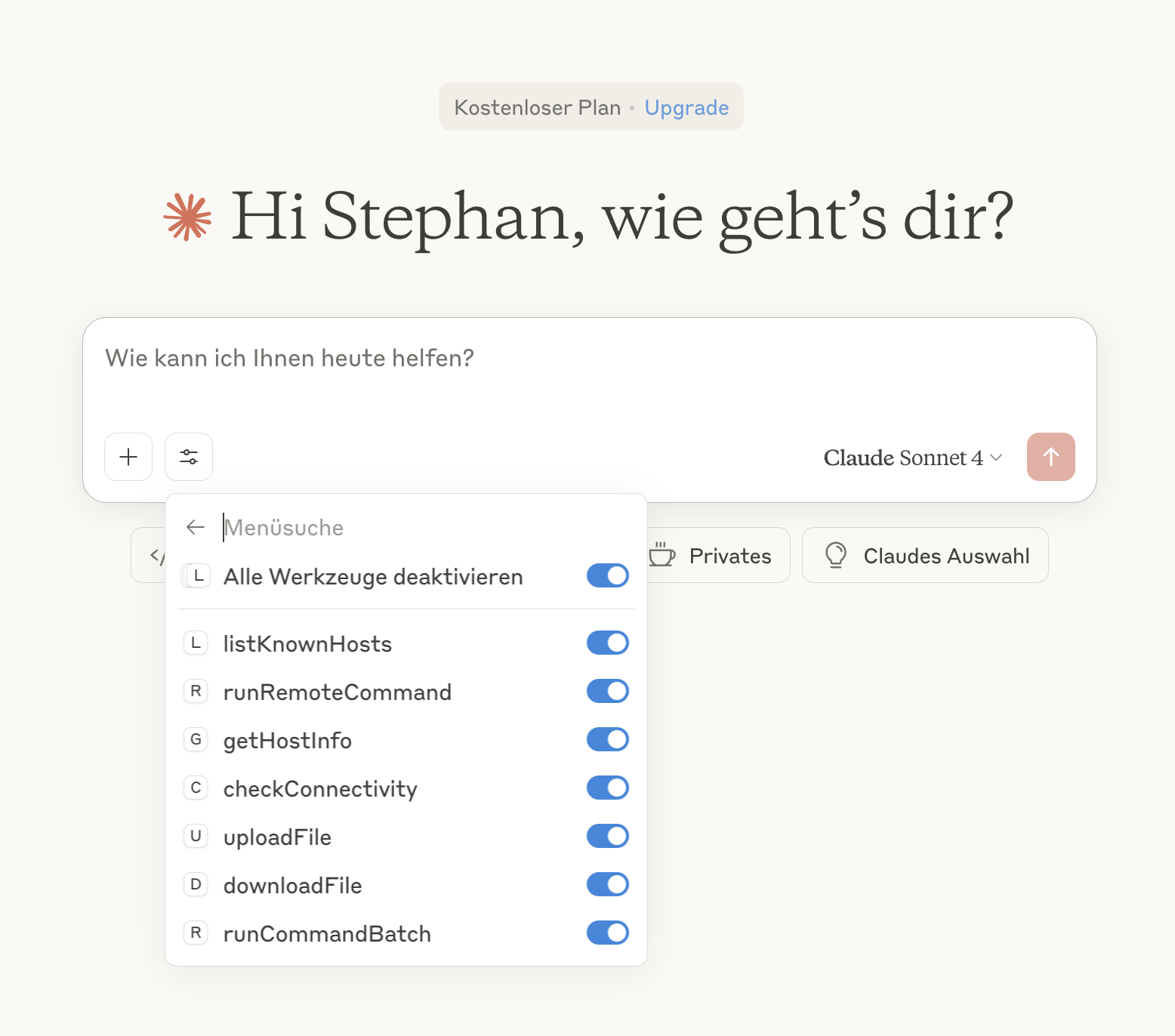
This screenshot demonstrates the MCP SSH Agent integrated with Claude, showing how the AI assistant can directly manage SSH connections and execute remote commands through the MCP protocol.
Key Features
Reliable SSH: Uses native
ssh/scpcommands instead of JavaScript SSH librariesAutomatic Discovery: Finds hosts from SSH config and known_hosts files
Full SSH Support: Works with SSH agents, keys, and all authentication methods
File Operations: Upload and download files using
scpBatch Commands: Execute multiple commands in sequence
Error Handling: Comprehensive error reporting with timeouts
Functions
The agent provides the following MCP tools:
listKnownHosts() - Lists all known SSH hosts, prioritizing entries from ~/.ssh/config first, then additional hosts from ~/.ssh/known_hosts
runRemoteCommand(hostAlias, command) - Executes a command on a remote host using
sshgetHostInfo(hostAlias) - Returns detailed configuration for a specific host
checkConnectivity(hostAlias) - Tests SSH connectivity to a host
uploadFile(hostAlias, localPath, remotePath) - Uploads a file to the remote host using
scpdownloadFile(hostAlias, remotePath, localPath) - Downloads a file from the remote host using
scprunCommandBatch(hostAlias, commands) - Executes multiple commands sequentially
Configuration Examples
Claude Desktop Integration
Here's how your Claude Desktop configuration should look:
Manual Server Configuration
If you prefer to run the server manually or integrate it with other MCP clients:
Requirements
Node.js 18 or higher
SSH client installed (
sshandscpcommands available)SSH configuration files (
~/.ssh/configand~/.ssh/known_hosts)
Usage with Claude Desktop
Once configured, you can ask Claude to help you with SSH operations like:
"List all my SSH hosts"
"Check connectivity to my production server"
"Run a command on my web server"
"Upload this file to my remote server"
"Download logs from my application server"
Claude will use the MCP SSH tools to perform these operations safely and efficiently.
Usage
The agent runs as a Model Context Protocol server over STDIO. When installed via npm, you can use it directly:
The server communicates via clean JSON over STDIO, making it perfect for MCP clients like Claude Desktop.
Advanced Configuration
Environment Variables
MCP_SILENT=true- Disable debug output (automatically set when used as MCP server)
SSH Configuration
The agent reads from standard SSH configuration files:
~/.ssh/config- SSH client configuration (supports Include directives)~/.ssh/known_hosts- Known host keys
Make sure your SSH keys are properly configured and accessible via SSH agent or key files.
Include Directive Support
The MCP SSH Agent fully supports SSH Include directives to organize your configuration across multiple files. However, there's an important SSH bug to be aware of:
⚠️ SSH Include Directive Bug Warning
SSH has a configuration parsing bug where Include statements must be placed at the beginning of your ~/.ssh/config file to work correctly. If placed at the end, SSH will read them but won't properly apply the included configurations.
✅ Correct placement (at the beginning):
❌ Incorrect placement (at the end) - won't work:
The MCP SSH Agent correctly processes Include directives regardless of their placement in the file, so you'll get full host discovery even if SSH itself has issues with your configuration.
Example ~/.ssh/config
Here's an example SSH configuration file that demonstrates various connection scenarios including Include directives:
This configuration demonstrates:
Global settings:
ServerAliveIntervalto keep connections aliveCustom ports: Non-standard SSH ports for security
Multiple users: Different user accounts for the same host (e.g.,
prodandroot@prod)Jump hosts: Using
ProxyJumpto access servers through bastion hostsIPv6 addresses: Modern networking support
Identity files: Specific SSH keys for different servers
Security options:
IdentitiesOnly yesto use only specified keys
How MCP SSH Agent Uses Your Configuration
The MCP SSH agent automatically discovers and uses your SSH configuration:
Host Discovery: All hosts from
~/.ssh/configare automatically availableNative SSH: Uses your system's
sshcommand, so all config options workAuthentication: Respects your SSH agent, key files, and authentication settings
Jump Hosts: Supports complex proxy chains and bastion host setups
Port Forwarding: Can work with custom ports and connection options
Example Usage with Claude Desktop:
"List my SSH hosts" → Shows all configured hosts including
prod,archive,web1.example.com, etc."Connect to archive server" → Uses the ProxyJump configuration automatically
"Run 'df -h' on web1.example.com" → Connects with the correct user, port, and key
"Upload file to database server" → Uses the specific identity file and port configuration
Troubleshooting
Common Issues
Command not found: Ensure
sshandscpare installed and in your PATHPermission denied: Check SSH key permissions and SSH agent
Host not found: Verify host exists in
~/.ssh/configor~/.ssh/known_hostsConnection timeout: Check network connectivity and firewall settings
Debug Mode
Run with debug output to see detailed operation logs:
SSH Key Setup Guide
For the MCP SSH Agent to work properly, you need to set up SSH key authentication. Here's a complete guide:
1. Creating SSH Keys
Generate a new SSH key pair (use Ed25519 for better security):
Important: When prompted for a passphrase, leave it empty (press Enter). The MCP SSH Agent cannot handle password-protected keys as it runs non-interactively.
This creates two files:
~/.ssh/id_ed25519(private key) - Keep this secret!~/.ssh/id_ed25519.pub(public key) - This gets copied to servers
2. Installing Public Key on Remote Servers
Copy your public key to the remote server's authorized_keys file:
3. Server-Side SSH Configuration
To enable secure key-only authentication on your SSH servers, edit /etc/ssh/sshd_config:
Add or modify these settings:
After editing, restart the SSH service:
4. Setting Correct Permissions
SSH is very strict about file permissions. Set them correctly:
On your local machine:
On the remote server:
5. Testing SSH Key Authentication
Test your connection before using with MCP SSH Agent:
6. Multiple Keys for Different Servers
You can create different keys for different servers:
Then configure them in ~/.ssh/config:
Security Best Practices
SSH Key Security
Never use password-protected keys with MCP SSH Agent
Never share private keys - they should stay on your machine only
Use Ed25519 keys when possible (more secure than RSA)
Create separate keys for different environments/purposes
Regularly rotate keys (every 6-12 months)
Server Security
Disable password authentication completely
Use non-standard SSH ports to reduce automated attacks
Limit SSH access to specific users with
AllowUsersChoose appropriate root login policy:
PermitRootLogin prohibit-password- Allows root access with SSH keys only (recommended for admin tasks)PermitRootLogin no- Completely disables root login (most secure, but requires sudo access)
Enable SSH key-only authentication for all accounts
Consider using jump hosts for additional security layers
Network Security
Use VPN or bastion hosts for production servers
Implement fail2ban to block brute force attempts
Monitor SSH logs regularly
Use SSH key forwarding carefully (disable when not needed)
Building Desktop Extensions
For developers who want to build DXT packages locally:
Prerequisites
Node.js 18 or higher
npm
Building DXT Package
This creates a .dxt file in the build/ directory that can be installed in Claude Desktop.
Publishing DXT Releases
To publish a new DXT release:
The DXT file will be available as a release asset for users to download and install.
Contributing
Contributions are welcome! Please feel free to submit a Pull Request.
License
MIT License - see LICENSE file for details.
Project Structure
About
This project is maintained by aionda.com and provides a reliable bridge between AI assistants and SSH infrastructure through the Model Context Protocol.