This server provides comprehensive access to Cisco Support APIs through the Model Context Protocol (MCP), enabling AI assistants to search and analyze Cisco product bugs, security vulnerabilities, lifecycle information, and support cases.
Core Capabilities:
Bug Search & Analysis: Search bugs by keyword, specific bug ID, product ID, product series, product name, and software releases with filtering by severity (1-6), status (Open, Fixed, Terminated), and modification date
Enhanced Analysis Tools: Smart search strategy recommendations, progressive multi-strategy searches, multi-severity searches, comprehensive product assessments combining bugs with lifecycle guidance, and version comparison for stability and security analysis
Product Information: Resolve product IDs to full names, serial number lookups for coverage and warranty info, and automatic version normalization (17.09.06 → 17.9.6)
Security & Lifecycle: Access PSIRT vulnerability data, security advisories, and End-of-Life (EoX) information for planning
Support Case Management: Create, update, and manage support cases with investigation tools
Software Recommendations: Get software suggestions, releases, and upgrade recommendations
Product Autocomplete: Search Cisco's internal product catalog using MCP Resources (requires browser session cookies)
Smart Bonding Integration: Experimental ticket management and problem code classification (requires special credentials)
Key Features:
8 Core Cisco Support APIs: Bug, Case, EoX, PSIRT, Product, Software, Serial, RMA with 46 implemented tools
10+ Specialized Prompts: Guided workflows for incident investigation, upgrade planning, security advisory research, and more with dynamic user elicitation support
Multiple Authentication Modes: stdio (no auth), Bearer token, OAuth 2.1 with PKCE and scope-based access control
Dual Transport Support: stdio mode for local clients (Claude Desktop) and HTTP mode for remote access
Production-Ready: Docker deployment, health monitoring, comprehensive logging, automatic OAuth2 token management, security headers (Helmet), CORS, input validation, and Server-Sent Events (SSE) for real-time updates
Provides access to Cisco Support APIs including Bug Search, Case Management, End-of-Life information, PSIRT security vulnerability data, Product information, and Software recommendations through 33 tools across 6 different Cisco APIs.
Offers alternative endpoint compatibility for N8N integration, allowing the MCP server to be used with N8N automation workflows.
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@mcp-cisco-supportsearch for bugs affecting Cisco Catalyst 9300 switches"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
Cisco Support MCP Server
A production-ready TypeScript MCP (Model Context Protocol) server for Cisco Support APIs with comprehensive security and dual transport support. This extensible server provides access to multiple Cisco Support APIs including Bug Search, Case Management, and End-of-Life information.
🚀 Current Features
Multi-API Support: 8 Cisco Support APIs fully implemented (46 total tools)
OAuth 2.1 Server: ✨ Production-grade authentication with fine-grained scope-based access control
ElicitationRequest Support: Dynamic user interaction for gathering missing parameters
Triple Auth Modes: stdio (no auth), Bearer token (simple), OAuth 2.1 (production)
Configurable API Access: Enable only the Cisco Support APIs you have access to
Specialized Prompts: 9 workflow prompts for guided Cisco support scenarios
Dual Transport: stdio (local MCP clients) and HTTP (remote server with auth)
OAuth2 Authentication: Automatic token management with Cisco API
Real-time Updates: Server-Sent Events for HTTP mode
TypeScript: Full type safety and MCP SDK integration
Production Security: Helmet, CORS, input validation, PKCE, scope validation
Docker Support: Containerized deployment with OAuth config volume mounts
Comprehensive Logging: Structured logging with timestamps
Related MCP server: MCPKit
📊 Supported Cisco APIs
The server supports the following Cisco Support APIs (configurable via SUPPORT_API environment variable):
API | Status | Tools | Description |
Enhanced Analysis ( | ⭐ RECOMMENDED | 6 tools | Advanced analysis tools for comprehensive product assessment |
Bug ( | ✅ Complete | 14 tools | Bug Search, Details, Product-specific searches + Enhanced tools |
Case ( | ✅ Complete | 4 tools | Support case management and operations |
EoX ( | ✅ Complete | 4 tools | End of Life/Sale information and lifecycle planning |
PSIRT ( | ✅ Complete | 8 tools | Product Security Incident Response Team vulnerability data |
Product ( | ✅ Complete | 3 tools | Product details, specifications, and technical information |
Software ( | ✅ Complete | 6 tools | Software suggestions, releases, and upgrade recommendations |
Serial ( | ✅ Complete | 3 tools | Serial number to coverage, warranty, and product information |
RMA ( | ✅ Complete | 3 tools | Return Merchandise Authorization tracking and management |
Smart Bonding ( | ⚠️ EXPERIMENTAL | 8 tools | Complete ticket lifecycle management and TSP codes (UNTESTED - requires special credentials) |
Implementation Status: 8/8 Core APIs complete (100%) with 46 total tools + 1 experimental API (8 tools)
Configuration Examples:
SUPPORT_API=enhanced_analysis- Enhanced analysis tools only (6 tools) ← RECOMMENDED for most usersSUPPORT_API=bug- All Bug API tools including enhanced analysis (14 tools)SUPPORT_API=bug,case,eox,psirt- Core support APIs (28 tools)SUPPORT_API=bug,case,eox,psirt,product,software- All implemented APIs (39 tools)SUPPORT_API=all- All available APIs (includes 2 placeholder APIs)
Quick Start
NPX Installation (Recommended)
Start in stdio mode for Claude Desktop:
Start HTTP server with authentication:
Generate Bearer token for HTTP mode:
Get help and see all options:
Environment Setup
Generate authentication token (for HTTP mode):
npx mcp-cisco-support --generate-token export MCP_BEARER_TOKEN=<generated_token>Set Cisco API credentials:
export CISCO_CLIENT_ID=your_client_id_here export CISCO_CLIENT_SECRET=your_client_secret_here export SUPPORT_API=bug,case,eox,psirt,product,software # All implemented APIs (recommended)Start the server:
# For Claude Desktop (stdio mode) npx mcp-cisco-support # For HTTP access (with authentication) npx mcp-cisco-support --http
Local Development
Claude Desktop Integration
Prerequisites
Get Cisco API Credentials:
Visit Cisco API Console
Create an application and get your Client ID and Secret
Ensure the application has access to the Bug API
Install Claude Desktop:
Download from Claude.ai
Make sure you're using a recent version that supports MCP
Step-by-Step Setup
Locate Claude Desktop Config File:
macOS:
~/Library/Application Support/Claude/claude_desktop_config.jsonWindows:
%APPDATA%\Claude\claude_desktop_config.json
Create or Edit the Config File:
{ "mcpServers": { "cisco-support": { "command": "npx", "args": ["-y", "mcp-cisco-support"], "env": { "CISCO_CLIENT_ID": "your_client_id_here", "CISCO_CLIENT_SECRET": "your_client_secret_here", "SUPPORT_API": "bug,product" } } } }Note: The
-yflag automatically accepts package installation, which is required for Claude Desktop since it runs in the background without user interaction.Optional Environment Variables:
Configure which APIs to enable with
SUPPORT_API:"enhanced_analysis"- Enhanced analysis tools only (recommended for most users)"bug"- Bug API only (default)"bug,product"- Bug + Product APIs (enables product autocomplete)"all"- All available APIs"bug,case,eox"- Multiple specific APIs
Product Autocomplete (optional, requires
SUPPORT_APIto includeproduct):"env": { "CISCO_CLIENT_ID": "your_client_id_here", "CISCO_CLIENT_SECRET": "your_client_secret_here", "SUPPORT_API": "bug,product", "CISCO_WEB_COOKIE": "JSESSIONID=...; OptanonConsent=..." }See the Product Autocomplete section for setup instructions.
Replace Your Credentials:
Replace
your_client_id_herewith your actual Cisco Client IDReplace
your_client_secret_herewith your actual Cisco Client Secret
Restart Claude Desktop:
Close Claude Desktop completely
Reopen the application
The MCP server will be automatically loaded
Verification
After setup, you should be able to:
Ask Claude about Cisco bugs:
"Search for bugs related to memory leaks in Cisco switches"Get specific bug details:
"Get details for Cisco bug CSCab12345"Search by product:
"Find bugs affecting Cisco Catalyst 3560 switches"
Example Usage in Claude Desktop
Once configured, you can ask Claude questions like:
Basic Bug Search:
"Search for recent bugs related to 'crash' in Cisco products"
"Find open bugs with severity 1 or 2"
"Show me bugs modified in the last 30 days"
Product-Specific Searches:
"Find bugs for product ID C9200-24P"
"Search for bugs in Cisco Catalyst 9200 Series affecting release 17.5.1"
"Show bugs fixed in software release 17.5.2"
Bug Details:
"Get full details for bug CSCab12345"
"Show me information about bugs CSCab12345,CSCcd67890"
Advanced Filtering:
"Find resolved bugs with severity 3 modified after 2023-01-01"
"Search for bugs in 'Cisco ASR 9000 Series' sorted by severity"
"Can you show me all the cisco bugs in the last 30 days for the product Cisco Unified Communications Manager (CallManager)?" (uses keyword search)
"Find bugs for Cisco Unified Communications Manager affecting releases 14.0 and 15.0" (uses product series search)
Claude will use the appropriate MCP tools to fetch real-time data from Cisco's Bug API and provide comprehensive responses with the latest information.
MCP Prompts
The server includes 10+ specialized prompts for guided Cisco support workflows:
🔍 cisco-high-severity-search - Search high-severity bugs by product or serial number
🚨 cisco-incident-investigation - Investigate symptoms and errors
🔄 cisco-upgrade-planning - Research issues before upgrades
🔧 cisco-maintenance-prep - Prepare for maintenance windows
🔒 cisco-security-advisory - Research security vulnerabilities
⚠️ cisco-known-issues - Check for software release issues
📋 cisco-case-investigation - Investigate support cases
⏰ cisco-lifecycle-planning - End-of-life planning
🎯 cisco-smart-search - Intelligent search with automatic refinement
✨ cisco-interactive-search - Interactive search with elicitation
Serial Number Support: Most prompts now accept either a product name OR a serial number. When you provide a serial number (e.g., "SAL09232Q0Z"), the server automatically looks up the product details and uses them for the search. This makes it easy to investigate issues when you have a device serial number but don't know the exact product model.
Each prompt provides structured investigation plans and expert recommendations.
Interactive Search with Elicitation
The cisco-interactive-search prompt demonstrates MCP's elicitation feature, allowing the server to dynamically request additional information from users during tool execution. This makes searches more natural and helps gather missing parameters without restarting requests.
Example Usage:
See examples/elicitation-example.md for detailed usage examples and ⚡ MCP Prompts for complete prompt documentation.
🔍 MCP Resources - Product Autocomplete
The server exposes Cisco data as MCP Resources for direct client access. This includes a new Product Autocomplete feature that lets you search Cisco's internal product catalog using your browser session cookie.
Available Product Resources
When SUPPORT_API includes product, the following resources are available:
Resource Templates (dynamic URIs):
cisco://products/{product_id}- Get product details by ID (e.g., C9300-24P, ISR4431)cisco://products/autocomplete/{search_term}- ✨ NEW: Search product catalog by name or model
Static Resources:
cisco://products/catalog- Product catalog overviewcisco://products/autocomplete-help- ✨ NEW: Setup instructions for product autocomplete
Product Autocomplete Setup
The product autocomplete feature requires your Cisco.com session cookie to access Cisco's internal API.
Quick Setup:
Log in to Cisco:
Log in with your Cisco account
Extract Your Cookie:
Open browser DevTools (F12)
Go to Application/Storage > Cookies
Select
https://bst.cloudapps.cisco.comCopy all cookie values
Set Environment Variable:
export CISCO_WEB_COOKIE="JSESSIONID=...; OptanonConsent=...; ..."Query Products:
cisco://products/autocomplete/4431 cisco://products/autocomplete/catalyst cisco://products/autocomplete/ASA
Cookie Lifecycle:
Typical Validity: 24 hours
Recommended Refresh: Daily before heavy use
Expiration Signs: 401/403 errors, "Cookie expired" messages
For detailed setup instructions, query the help resource:
Example Response
Query: cisco://products/autocomplete/4431
Security Best Practices
✅ Never commit cookies - they're like passwords
✅ Use .env file - already in .gitignore
✅ Refresh regularly - cookies expire after ~24 hours
✅ Monitor activity - check your Cisco account
✅ Use dedicated account - not your primary login
Usage in Claude Desktop
Ask Claude:
"Show me the help for product autocomplete"
"Search for Cisco product 4431 using autocomplete"
"What is the full name of product ISR4431?"
"Find products matching 'catalyst switch'"
See docs/PRODUCT_AUTOCOMPLETE_SOLUTIONS.md for implementation details and docs/CISCO_COOKIE_ANALYSIS.md for cookie lifecycle information.
⚠️ Smart Bonding Customer API (EXPERIMENTAL/UNTESTED)
The server includes experimental support for Cisco's Smart Bonding Customer API for ticket management and problem code classification. This feature is UNTESTED and requires special credentials obtained through your Cisco Account Manager.
Smart Bonding Features
Available Tools (8 total):
get_smart_bonding_tsp_codes- Retrieve TSP (Technology, Sub-Technology, Problem Code) details for ticket classificationpull_smart_bonding_tickets- Retrieve ticket updates from Cisco that haven't been pulled yetcreate_smart_bonding_ticket- Create a new support ticket (returns upload credentials in response)update_smart_bonding_ticket- Add work notes and update ticket statusupload_file_to_smart_bonding_ticket- Upload files using credentials from ticket creation (HTTPS PUT to cxd.cisco.com)escalate_smart_bonding_ticket- Escalate critical issues to Ciscoresolve_smart_bonding_ticket- Mark tickets as resolved with resolution notesclose_smart_bonding_ticket- Close completed tickets with diagnosis and solution
File Upload Process
Smart Bonding uses a separate upload mechanism from the REST API:
Create ticket → Response includes upload credentials (Field80-82)
Save credentials → Cannot be retrieved later!
Upload files → Use
upload_file_to_smart_bonding_tickettool or curl72-day expiration → Token expires 72 days after creation
Upload credentials provided in ticket creation response:
Field80: Upload domain (e.g., cxd.cisco.com)
Field81: Authentication token (password)
Field82: Token expiration timestamp
Files cannot be modified after upload - submit new files for corrections.
Authentication Differences
Smart Bonding API uses a different authentication system than standard Cisco Support APIs:
Feature | Standard Support APIs | Smart Bonding API |
OAuth2 Endpoint |
|
|
Token Validity | 12 hours | 1 hour |
Credentials | Self-service via Cisco Developer Portal | Contact Cisco Account Manager |
Environment Variables |
|
|
Configuration
Obtain Credentials - Contact your Cisco Account Manager to request Smart Bonding API access
Set Environment Variables:
export SMART_BONDING_CLIENT_ID=your_smart_bonding_client_id export SMART_BONDING_CLIENT_SECRET=your_smart_bonding_client_secret export SMART_BONDING_ENV=production # or 'staging' for test environment export SUPPORT_API=smart_bonding # Enable Smart Bonding APIUse Smart Bonding Tools:
Get TSP codes for ticket classification
Pull new ticket updates
Create/update tickets with standardized problem categorization
Important Notes
⚠️ EXPERIMENTAL/UNTESTED - This implementation has not been tested with live Smart Bonding credentials
⚠️ Separate Credentials Required - Smart Bonding uses different OAuth2 credentials than standard Support APIs
⚠️ Not Included in - Must be explicitly enabled with
SUPPORT_API=smart_bonding⚠️ Special Access Required - Contact Cisco Account Manager for credential provisioning
Base URLs differ for staging vs production environments
Supports correlation IDs for end-to-end request traceability
Example Usage
For complete implementation details and API architecture, see SMART_BONDING_IMPLEMENTATION.md.
Screenshots
Claude Desktop Integration
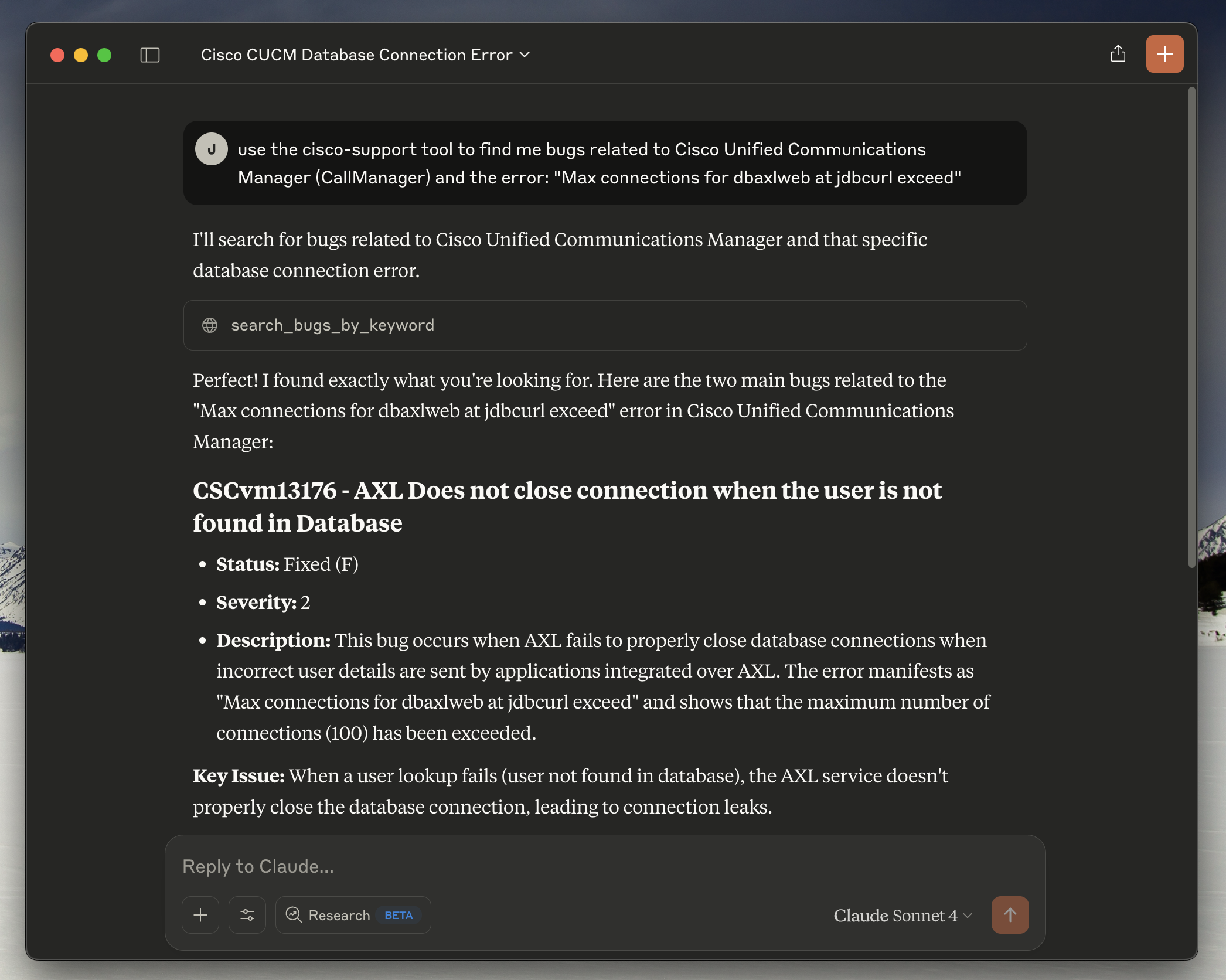
Claude Desktop successfully connected to the Cisco Support MCP server, demonstrating the bug search functionality with real-time responses from Cisco's Bug API.
MCP Inspector
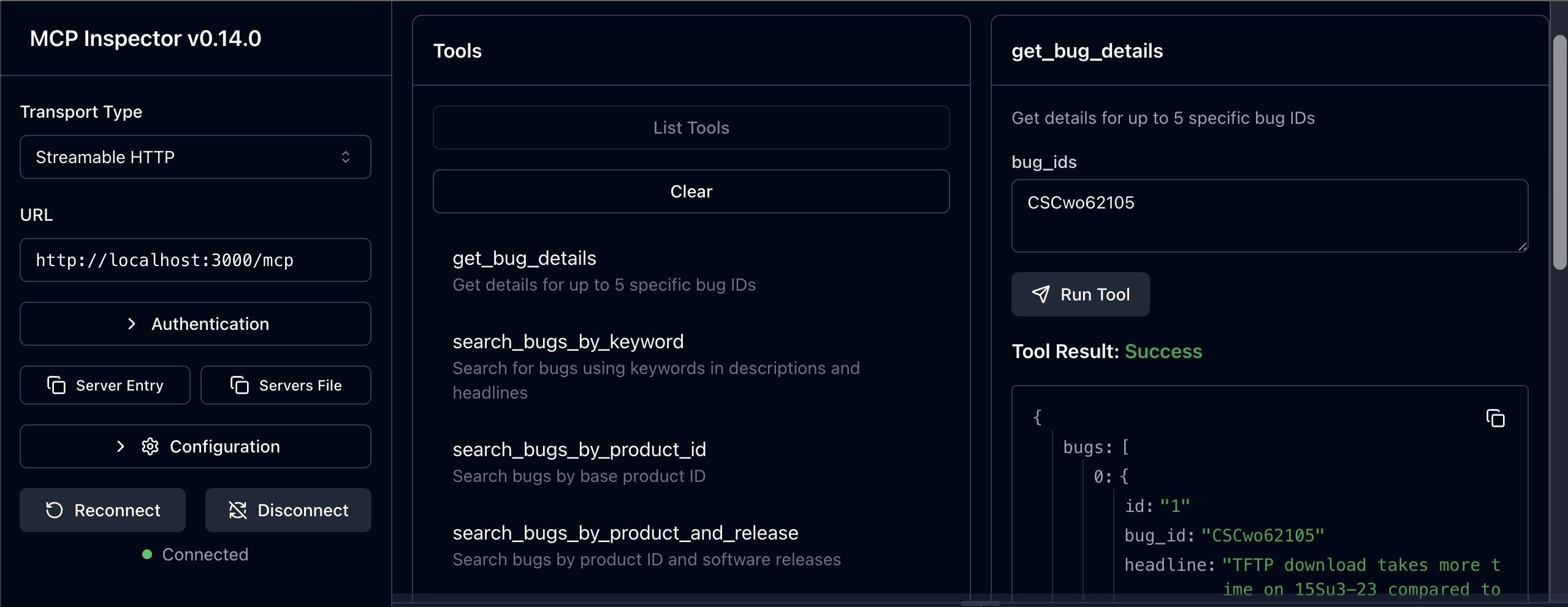
MCP Inspector v0.14.0+ showing the available tools and server connectivity testing capabilities.
Alternative Installation Methods
Global Installation
If you prefer to install globally instead of using npx:
Then use this config:
Local Installation
For development or custom setups:
Then use this config:
Troubleshooting
Common Issues
"Command not found" errors:
Ensure Node.js 18+ is installed
Try global installation:
npm install -g mcp-cisco-supportVerify the path in your config file
Authentication failures:
Double-check your Client ID and Secret
Ensure your Cisco API app has Bug API access
Check for typos in the config file
MCP server not loading:
Restart Claude Desktop completely
Check the config file syntax with a JSON validator
Look for Claude Desktop logs/error messages
Permission errors:
Ensure the config file is readable
On macOS/Linux, check file permissions:
chmod 644 claude_desktop_config.json
Debugging
Test the server manually:
npx mcp-cisco-supportThis should start the server in stdio mode without errors.
Validate your config: Use a JSON validator to ensure your config file is properly formatted.
Check Claude Desktop logs:
Look for MCP-related error messages in Claude Desktop
The app usually shows connection status for MCP servers
Monitor logs in real-time (macOS):
# Follow logs in real-time tail -n 20 -F ~/Library/Logs/Claude/mcp*.logOn Windows:
# Check logs directory %APPDATA%\Claude\logs\
Getting Help
Issues: GitHub Issues
Cisco API: Cisco Developer Documentation
MCP Protocol: Model Context Protocol
Docker Deployment
🔐 Security
stdio mode: No authentication (Claude Desktop, local clients)
HTTP mode: Bearer token authentication required
See 🔒 Security Guide for complete security documentation.
Configuration
Environment Variables
Create a .env file with your configuration:
OAuth 2.1 Authentication (Advanced)
For production-grade authentication with fine-grained access control, use OAuth 2.1 mode:
Quick Start
Configuration Files
config/oauth-clients.json - Client configuration (can be version controlled):
config/oauth-secrets.json - Client secrets (gitignored, never commit):
OAuth Scopes
Control API access with fine-grained scopes:
Scope | API Access | Description |
| All APIs | Full access to all MCP tools |
| Bug API | Bug search and details only |
| Case API | Support case management only |
| EoX API | End-of-life information only |
| Security API | Security advisories only |
| Product API | Product information only |
| Software API | Software suggestions only |
| Serial API | Serial number lookups only |
| RMA API | Return authorization only |
Best Practice: Grant only the scopes each application needs (principle of least privilege).
Environment Variables
Point to custom config file locations:
OAuth Endpoints
When running in OAuth 2.1 mode, the server provides:
GET /.well-known/oauth-authorization-server- OAuth discovery metadataGET /authorize- Authorization endpoint (displays consent page)POST /authorize/approve- Authorization approvalPOST /token- Token endpoint (PKCE required)POST /register- Dynamic client registration (if enabled)
See docs/OAUTH_CLIENTS_CONFIG.md for complete OAuth 2.1 documentation.
Claude Desktop Integration
Complete configuration for Claude Desktop:
Docker Configuration
Option 1: Bearer Token Authentication
Option 2: OAuth 2.1 Authentication (Production)
Option 3: Without Authentication (Development Only)
Docker Compose with OAuth 2.1:
API Endpoints
Endpoint | Method | Description |
| GET | Server information and available endpoints |
| POST | Main MCP endpoint (JSON-RPC over HTTP) |
| POST | Alternative MCP endpoint for N8N compatibility |
| GET | SSE connection with session management |
| POST | Legacy SSE message endpoint (deprecated) |
| POST | Session-specific MCP message endpoint |
| GET | Simple ping endpoint for connectivity testing |
| GET | Health check with detailed status |
📚 Documentation
For detailed information, see our comprehensive GitHub Wiki:
📋 Available Tools - Complete reference for all 46 MCP tools across 8 APIs
🔧 Advanced Configuration - Environment variables and deployment options
🔒 Security Guide - Authentication, tokens, and security best practices
🚀 Docker Deployment - Containerized deployment and production setup
🌐 SSE Integration - Server-Sent Events and real-time communication
🧪 Testing Framework - Comprehensive testing and validation
🔧 Development Guide - Contributing, architecture, and API development
🚨 Troubleshooting Guide - Common issues and debugging
⚡ MCP Prompts - Guided workflows for Cisco support scenarios
Usage Examples
cURL Examples
JavaScript Client Example
Health Monitoring
The server provides a comprehensive health check endpoint:
Response includes:
Server status
OAuth2 token status
Memory usage
Uptime
Active SSE connections
Security Features
Helmet: Security headers
CORS: Cross-origin resource sharing
Input Validation: Schema-based validation
Non-root Execution: Docker security
Environment Variables: Secure credential storage
Troubleshooting
Common Issues
OAuth2 Authentication Failed
Verify
CISCO_CLIENT_IDandCISCO_CLIENT_SECRETCheck network connectivity to
https://id.cisco.com
API Calls Failing
Check token validity at
/healthVerify network access to
https://apix.cisco.com
Docker Issues
Ensure environment variables are set
Check Docker logs:
docker-compose logs
Logs
Structured JSON logs include:
Timestamp
Log level (info, error, warn)
Message
Additional context data
Testing
Running Tests
Test Structure
The test suite includes:
Authentication Tests (
tests/auth.test.js): OAuth2 authentication, token management, error handlingMCP Tools Tests (
tests/mcp-tools.test.js): All 8 MCP tools, error handling, paginationSetup (
tests/setup.js): Test environment configuration
Recent Test Fixes
The following issues were identified and resolved in the test suite:
✅ Fixed Issues
Token Refresh Logic
Problem: Token expiry calculation was incorrect in
getValidToken()Solution: Fixed condition to properly check if token is within refresh margin
Impact: Proper token caching and refresh behavior
Multiple Bug IDs Handling
Problem: State leakage between tests causing mock sequence mismatches
Solution: Implemented
resetServerState()function for proper cleanupImpact: Consistent test results across multiple runs
Search Tools Implementation
Problem: Same state management issue affecting keyword search and other tools
Solution: Proper server state reset between tests
Impact: All 8 MCP tools now work correctly
Error Handling
Problem: API errors and network timeouts not properly converted to MCP error responses
Solution: Enhanced error handling in
handleMCPMessage()functionImpact: Proper error responses for client applications
Authentication Failure Scenarios
Problem: Health endpoint returning 200 instead of 503 on auth failures
Solution: Module cache clearing and proper state isolation
Impact: Correct health status reporting
Test State Management
Problem: Module-level variables persisting between tests
Solution: Added
resetServerState()export and proper module cache clearingImpact: True test isolation and reliable test results
Test Configuration
Jest: Using Jest with
--forceExitflag for main test runsState Reset: Each test gets a fresh server instance with clean state
Mock Management: Proper fetch mocking with correct sequence handling
Test Isolation: Module cache clearing prevents state leakage
Key Implementation Details
Native fetch: Uses Node.js native fetch instead of external libraries
Token Management: 12-hour token validity with 30-minute refresh margin
Error Handling: Comprehensive error handling with proper MCP error responses
Security: Helmet security headers, CORS support, input validation
Logging: Structured JSON logging with timestamps
Development
Project Structure
Development Commands
Performance Considerations
Token caching reduces API calls
Pagination limits results to 10 per page
SSE heartbeat every 30 seconds keeps connections alive
Request timeout set to 30 seconds
Security Notes
Never commit
.envfile to version controlUse environment variables for all secrets
Review Cisco API usage limits and terms
Monitor logs for suspicious activity
API Reference
Authentication
OAuth2 URL:
https://id.cisco.com/oauth2/default/v1/tokenGrant Type:
client_credentialsToken Validity: 12 hours
Auto-refresh: 30 minutes before expiry
Bug API Base URL
Base URL:
https://apix.cisco.com/bug/v2.0
MCP Protocol
The server implements the Model Context Protocol with these methods:
initialize: Initialize MCP connectiontools/list: List available toolstools/call: Execute a tool
Example MCP message:
Health Monitoring
The server provides a comprehensive health check endpoint:
Response includes server status, OAuth2 token status, memory usage, uptime, and active connections.
Testing
Comprehensive Jest-based testing framework with:
✅ 46/46 tools tested - All MCP tools across 8 APIs
✅ Mock & Real API testing - Unit tests with mocks + integration tests with live APIs
✅ Individual tool testing - Standalone test runner for development
See 🧪 Testing Framework for complete testing documentation.
License
MIT License - see LICENSE file for details.
Contributing
Fork the repository
Create a feature branch
Make your changes
Add tests for new functionality
Ensure all tests pass:
npm testSubmit a pull request
Support
Resources
📖 Complete Documentation - Comprehensive project documentation
📚 Wiki - Detailed guides and troubleshooting
🐛 Issues - Report bugs and request features
External Resources
🔧 Cisco Developer Documentation - Official API documentation
🔒 Cisco PSIRT Documentation - Security vulnerability API documentation
💬 Cisco Services Discussions - Community support and API discussions
🌐 MCP Protocol - Model Context Protocol specification