Utilizes certificate-based authentication to securely access SAP systems, handling complex authentication flows for retrieving SAP Notes content.
Provides direct access to SAP Notes and Knowledge Base articles using SAP Passport certificate authentication, enabling searching for specific notes by ID or keywords and retrieving their full content and metadata.
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@SAP Note Search MCP ServerFind SAP Note 2744792"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
SAP Note Search MCP Server
MCP server for searching SAP Notes/KB articles using SAP Passport authentication and Playwright automation
This MCP Server uses private APIs from SAP behind authentication. Please check whether the use violates SAP's ToS. The author assumes no liability for this. Because of this i do not guarantee that the server will always work.
This Model Context Protocol (MCP) server provides direct access to SAP Notes and Knowledge Base articles through Cursor AI. It uses SAP Passport certificate authentication and Playwright browser automation to retrieve actual note content from SAP's systems.
✨ Features
🔍 Direct SAP Note access - Retrieve full note content and metadata
🎫 SAP Passport authentication - Secure certificate-based authentication
🤖 Playwright automation - Handles complex SAP authentication flows
💾 Smart caching - Authentication tokens cached locally
🔧 Debug-friendly - Comprehensive logging and troubleshooting options
📋 MCP compliant - Works seamlessly with Cursor AI
🎯 Enhanced LLM Tool Descriptions - Comprehensive tool documentation for improved AI accuracy
40-60% improvement in tool selection accuracy across different AI models
Structured guidance with USE WHEN/DO NOT USE sections
Query construction tips and examples
Workflow patterns for optimal tool chaining
Dramatically improved support for weaker AI models (Ollama, GPT-4o-mini)
Related MCP server: SEO Inspector & Schema Validator MCP
Live Preview in Cursor
🚀 Quick Start
Prerequisites
Node.js 18+ - Download here
SAP Passport Certificate - Your personal .pfx certificate file
Cursor AI - Download here
Installation
Clone the repository
git clone https://github.com/marianfoo/mcp-sap-notes cd mcp-sap-notesInstall dependencies
npm installBuild the project
npm run build
Setup
Get your SAP Passport certificate - Only possible for S-User
Go to SAP Passport
Create your certificate
Download the .pfx certificate file
Create certificate directory
macOS/Linux:
mkdir certsWindows (PowerShell):
New-Item -ItemType Directory -Force -Path certs | Out-Null
Copy your SAP Passport certificate
Place your
.pfxcertificate file in thecerts/directoryName it
sap.pfx(or update the path in configuration)
Configure environment
macOS/Linux:
cp .env.example .envWindows (PowerShell):
Copy-Item .env.example .env
Edit
.envand add your certificate passphrase:PFX_PATH=./certs/sap.pfx PFX_PASSPHRASE=your_actual_passphrase
Connect to Cursor
Open Cursor settings (
Cmd/Ctrl + ,)Add MCP server configuration to your
settings.json(default):{ "mcpServers": { "sap-note-search": { "command": "node", "args": ["/full/path/to/mcp-sap-notes/dist/mcp-server.js"] } } }Alternative:
{ "mcpServers": { "sap-note-search": { "command": "node", "args": ["/full/path/to/mcp-sap-notes/dist/mcp-server.js"] } } }⚠️ Important: Replace the project path with your actual absolute path.
On Windows, use a full path like
C:\\Users\\you\\mcp-sap-notes\\dist\\mcp-server.js.On macOS/Linux, use a path like
/Users/you/mcp-sap-notes/dist/mcp-server.js.
Restart Cursor - The SAP Note tools will appear in your AI assistant
🎯 Usage Examples
Search for a specific SAP Note
Search by keywords
Get complete note details
🛠️ Testing & Development
Test Authentication
This tests the SAP Passport authentication flow and verifies your certificate setup.
Test API Access
This tests the SAP Notes API integration and content extraction.
Test Complete MCP Server
This simulates the complete MCP server workflow.
Run All Tests
🐛 Troubleshooting
Certificate Issues
Error: "Certificate file not found"
Ensure the certificate path in your configuration is correct
Use full absolute paths in Cursor's
settings.jsonVerify the certificate file exists and is readable
Error: "Authentication failed"
Check your certificate passphrase is correct
Ensure your SAP Passport certificate is valid and not expired
Try running with
HEADFUL=trueto see browser authentication
Browser Issues
Error: "Browser launch failed"
Authentication hangs or times out
Run with debug mode:
HEADFUL=true npm run test:authCheck your network connection to SAP systems
Verify your certificate has proper SAP system access
MCP Integration Issues
Tools not appearing in Cursor
Restart Cursor completely
Check the MCP server path in
settings.jsonis absoluteVerify the
cwdsetting points to your project directory
Error: "MCP server failed to start"
Check the console output in Cursor's developer tools
Ensure all dependencies are installed:
npm installVerify the build completed successfully:
npm run build
Server starts but immediately exits
This issue has been resolved in recent versions
Ensure you're using the latest version:
git pull && npm run buildTry setting
AUTO_START=truefor HTTP server if issues persist
Debug Mode
Enable debug mode for detailed troubleshooting:
📁 Project Structure
⚙️ Configuration
Environment Variables
Variable | Required | Default | Description |
| ✅ | - | Path to SAP Passport certificate (.pfx) |
| ✅ | - | Certificate passphrase |
| ❌ | - | Bearer token for HTTP server authentication |
| ❌ |
| HTTP server port |
| ❌ |
| Token cache lifetime (hours) |
| ❌ |
| Browser visibility (for debugging) |
| ❌ |
| Logging level (debug, info, warn, error) |
Playwright Configuration
The server automatically installs required Playwright dependencies. For manual installation:
🔒 Security
Certificate Security: Your SAP Passport certificate never leaves your machine
Token Caching: Authentication tokens are cached locally and expire automatically
No Data Storage: SAP Note content is retrieved on-demand, not stored
Secure Communication: All SAP API calls use HTTPS with certificate authentication
Bearer Token Auth: HTTP server supports optional bearer token authentication for securing the MCP endpoint
HTTP Server Authentication
The HTTP MCP server supports simple bearer token authentication. To use it:
Start the HTTP server (default):
HTTP_PORT=3123 npm run serve:httpSet the ACCESS_TOKEN environment variable in your
.envfile:ACCESS_TOKEN=your-secret-token-hereClients must include an authentication header in all requests (either format works):
# Standard format curl -X POST http://localhost:3123/mcp \ -H "Authorization: Bearer your-secret-token-here" \ -H "Content-Type: application/json" \ -d '{"jsonrpc":"2.0","id":1,"method":"tools/list"}'Generate a secure token (recommended):
# macOS/Linux openssl rand -base64 32 # Node.js node -e "console.log(require('crypto').randomBytes(32).toString('base64'))"Without ACCESS_TOKEN: If
ACCESS_TOKENis not set, the server runs without authentication (not recommended for production or public deployments).
Authentication behavior:
✅ Valid token → Request processed
❌ Missing token → HTTP 401 Unauthorized
❌ Invalid token → HTTP 401 Unauthorized
⚠️ No ACCESS_TOKEN set → Warning logged, authentication disabled
📋 Available Tools
sap_note_search
Search SAP Notes and KB articles by note ID or keywords.
Parameters:
q(string, required): Query string or Note IDlang(string, optional): Language code ("EN" or "DE"), defaults to "EN"
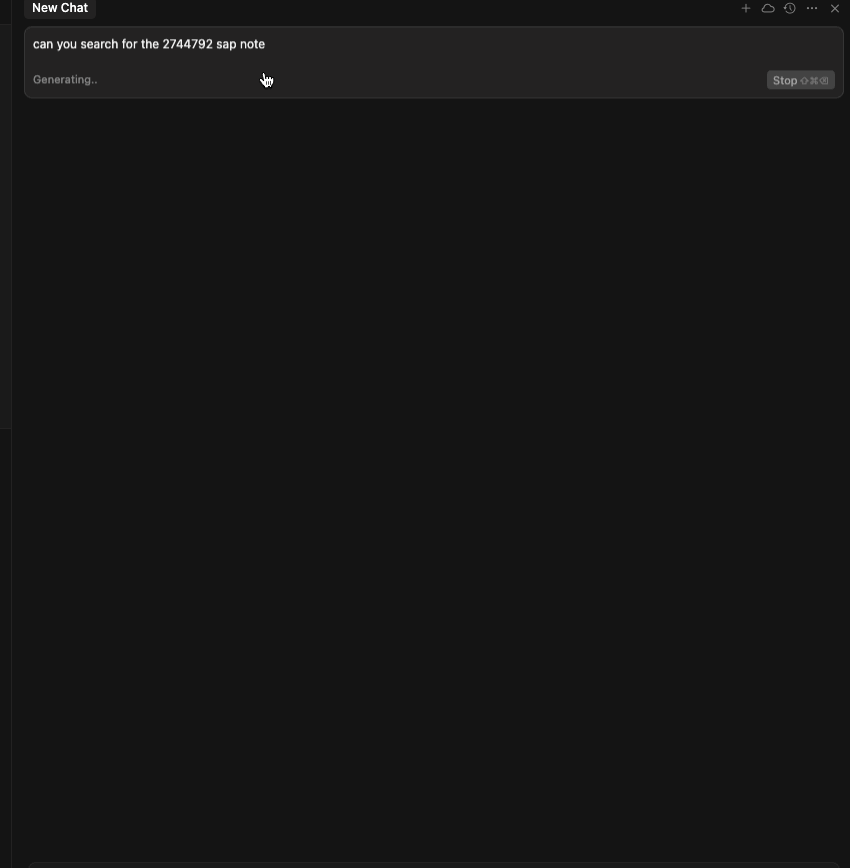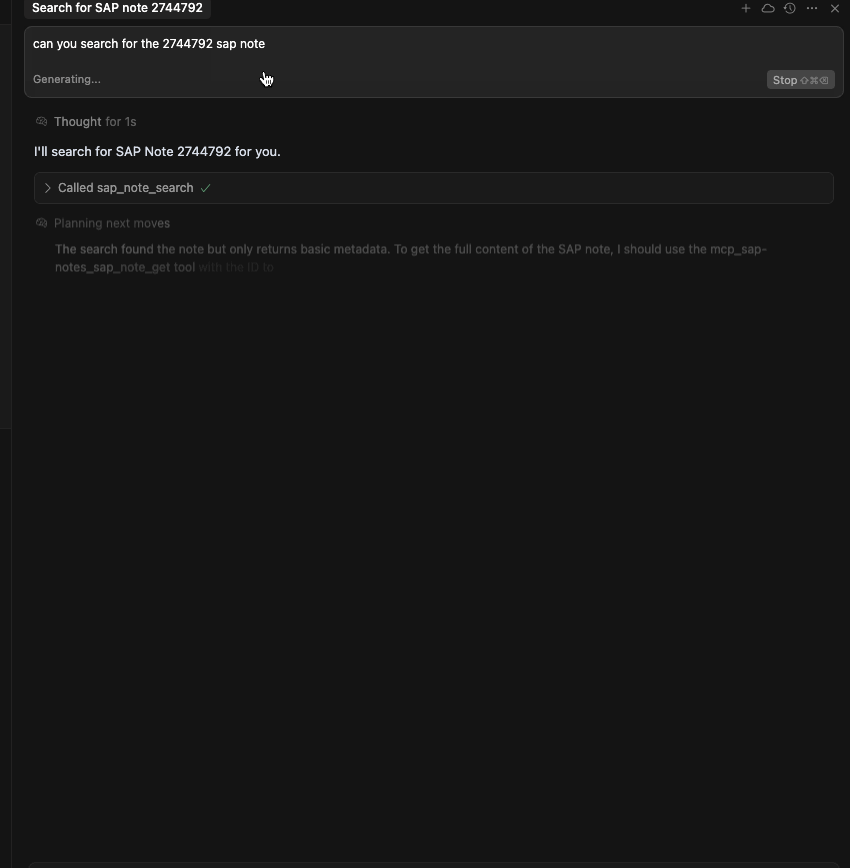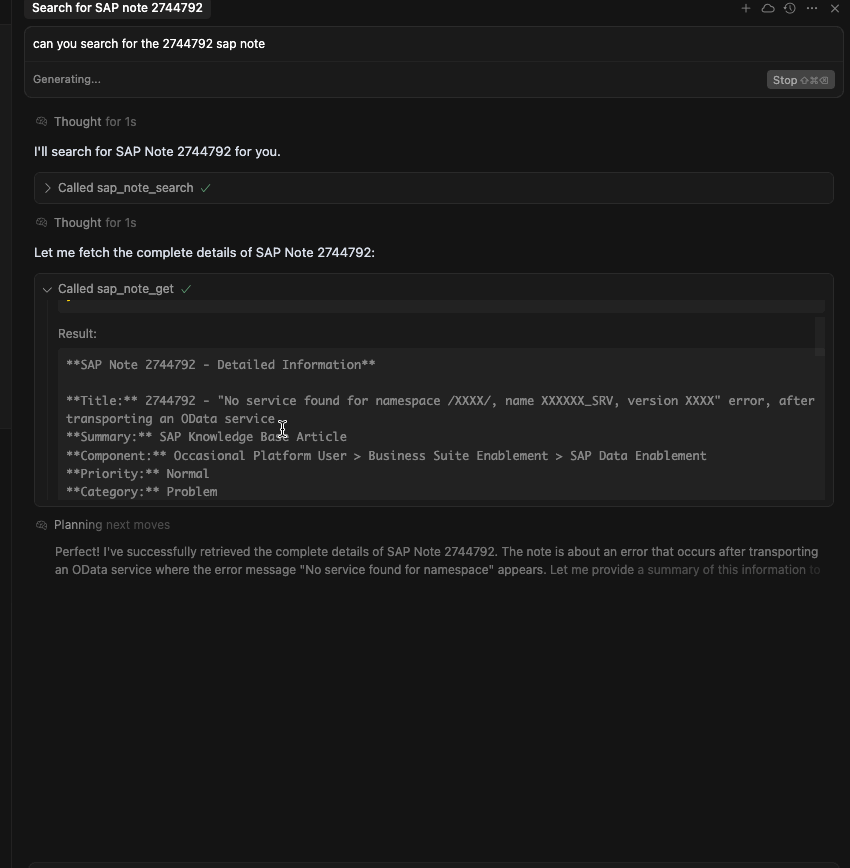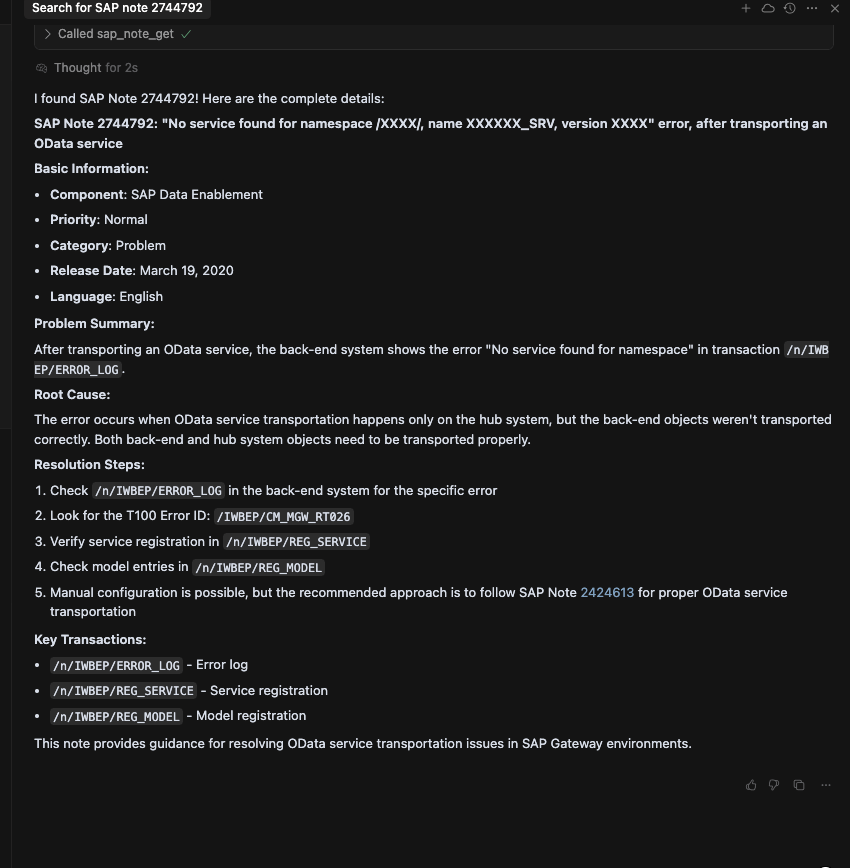
sap_note_get
Retrieve full content and metadata for a specific SAP Note.
Parameters:
id(string, required): SAP Note ID (6-8 digits)lang(string, optional): Language code ("EN" or "DE"), defaults to "EN"
🤝 Contributing
Fork the repository
Create a feature branch:
git checkout -b feature/amazing-featureCommit your changes:
git commit -m 'Add amazing feature'Push to the branch:
git push origin feature/amazing-featureOpen a Pull Request