Provides tools for searching GitHub repositories, listing repository files, and retrieving file content to analyze repositories for CVE research and proof-of-concept discovery
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@Risky Business MCP Servercheck if CVE-2024-12345 is being actively exploited"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
Risky Business AI MCP Server
A comprehensive Model Context Protocol (MCP) server for cybersecurity vulnerability assessment, providing tools to search GitHub repositories, query NIST NVD, access CISA's Known Exploited Vulnerabilities catalog, and analyze repository contents for CVE research and proof-of-concept discovery.
📹 Demo
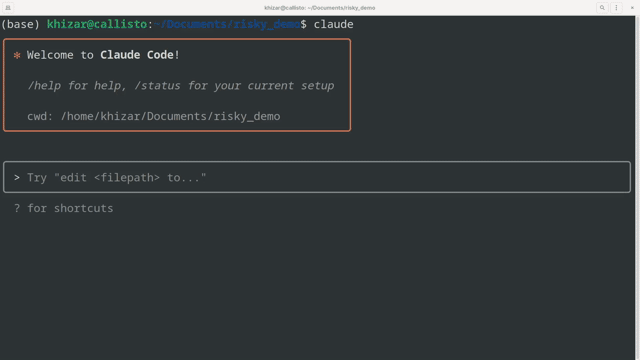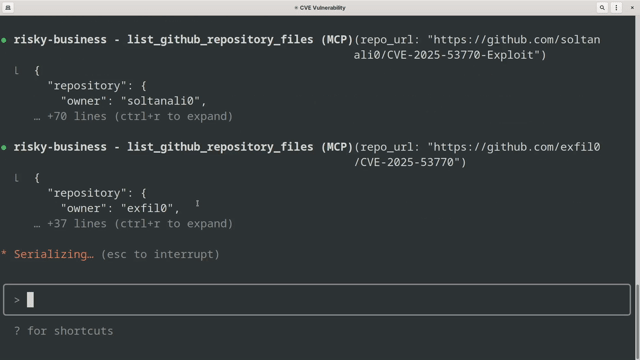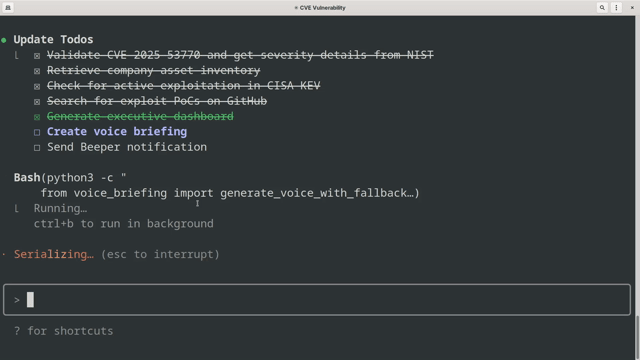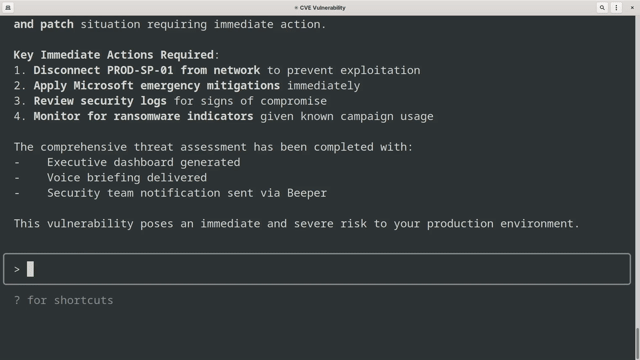
Demo Workflow
The demo demonstrates a complete vulnerability assessment for CVE-2025-53770:
✅ Validate CVE-2025-53770 and retrieve severity information from NIST
✅ Analyze business impact by checking company asset inventory
✅ Check for active exploitation in CISA KEV database
✅ Search for proof-of-concept exploits on GitHub
✅ Generate executive dashboard with findings
✅ Create and deliver voice briefing
✅ Send summary to Beeper chat
Sample Alert Message (Sent via Beeper)
Related MCP server: OSSInsight MCP Server
🛠️ Tools
search_github_repositories
Search GitHub repositories using the GitHub API.
Parameters:
query(string, required): Search query with keywords and qualifierssort(string, optional): Sort by "stars", "forks", "help-wanted-issues", "updated", or "best-match" (default)order(string, optional): "desc" (default) or "asc"per_page(integer, optional): Results per page, 1-100 (default: 5)page(integer, optional): Page number (default: 1)
get_cve_from_nist
Query NIST National Vulnerability Database for CVE details.
Parameters:
cve_id(string, required): CVE identifier (e.g., "CVE-2023-1234" or "2023-1234")
Returns: CVSS scores, severity ratings, CWE mappings, affected products (CPE), and references.
search_kev
Search CISA's Known Exploited Vulnerabilities catalog.
Parameters:
query(string, required): Search term (CVE ID, vendor, product, or keyword)field(string, optional): Field to search - "all", "cve_id", "vendor", "product", "vulnerability_name", "date_added" (default: "all")max_results(integer, optional): Maximum results 1-50 (default: 10)
Returns: Matching KEV entries with exploitation details and ransomware campaign indicators.
list_github_repository_files
List all files in a GitHub repository.
Parameters:
repo_url(string, required): GitHub repository URL (e.g., "https://github.com/owner/repo")branch(string, optional): Branch name (default: "main")
Returns: Complete file tree with paths, types, and SHA hashes.
get_github_file_content
Retrieve specific file content from a GitHub repository.
Parameters:
repo_url(string, required): GitHub repository URLfile_path(string, required): Path to file (e.g., "src/exploit.py")branch(string, optional): Branch name (default: "main")
Returns: File content (text or binary indicator) with metadata.
📝 Prompts
cve_repository_search
Generate targeted search strategies for specific CVE numbers.
Parameters:
cve_number(string, required): CVE identifier (e.g., "CVE-2023-1234")include_poc(boolean, optional): Include PoC-specific terms (default: true)
advanced_cve_search_strategies
Comprehensive guide for advanced CVE repository searching techniques.
📊 Resources
kev://cisa/catalog
Access the complete CISA Known Exploited Vulnerabilities catalog with active exploitation data.
assets://company/inventory
Company asset inventory for vulnerability impact assessment, including environment, criticality, and vendor information.
🚀 Quick Start
Prerequisites
Python 3.8+
uv(recommended) orpipOptional: GitHub Personal Access Token for higher API rate limits
Optional: NIST API Key for increased rate limits
Installation
Clone the repository
Set up Python virtual environment
Optional: Set up API authentication
Running the Server
With virtual environment activated:
Development mode (with MCP Inspector):
Claude Desktop Integration
Add the server to your Claude Desktop configuration:
macOS/Linux:
Windows:
Configuration:
Environment Variables
Variable | Description | Required |
| GitHub Personal Access Token for authentication | No (but recommended) |
| NIST NVD API key for increased rate limits | No (optional) |
🤝 Contributing
Fork the repository
Create a feature branch
Make your changes
Add tests if applicable
Submit a pull request
📄 License
This project is licensed under the MIT License - see the LICENSE file for details.
Disclaimer: This tool is for legitimate security research and educational purposes. Users are responsible for ensuring their use complies with applicable laws and GitHub's terms of service.