This server provides read-only access to your TrainingPeaks training data through natural conversation with Claude, enabling workout analysis, performance tracking, and fitness trend monitoring.
Query workouts - List and filter workouts by date range (planned, completed, or all) with up to 90 days per query
Analyze workout details - Get detailed metrics for individual workouts including power, heart rate, cadence, and TSS
Track personal records - View cycling PRs (5-second to 90-minute power) and running PRs (400m to marathon pace)
Find workout PRs - Identify which personal records were set during specific training sessions
Monitor fitness trends - Track CTL (fitness), ATL (fatigue), and TSB (form) over time to assess training load and race readiness
Compare performance over time - Analyze FTP progression, TSS patterns, training distribution, and form trends
Check authentication - Verify connection status when troubleshooting
Access athlete profile - Retrieve basic profile information (rarely needed)
Note: All access is read-only. The server cannot create, modify, or delete workouts or change any TrainingPeaks settings. Authentication uses secure cookie storage with no API approval required.
Click on "Install Server".
Wait a few minutes for the server to deploy. Once ready, it will show a "Started" state.
In the chat, type
@followed by the MCP server name and your instructions, e.g., "@TrainingPeaks-MCPshow me my workouts from last week"
That's it! The server will respond to your query, and you can continue using it as needed.
Here is a step-by-step guide with screenshots.
TrainingPeaks MCP Server
Connect TrainingPeaks to Claude and other AI assistants via the Model Context Protocol (MCP). Query your workouts, analyze training load, compare power data, and track fitness trends through natural conversation.
No API approval required. The official Training Peaks API is approval-gated, but this server uses secure cookie authentication that any user can set up in minutes. Your cookie is stored in your system keyring, never transmitted anywhere except to TrainingPeaks.
What You Can Do
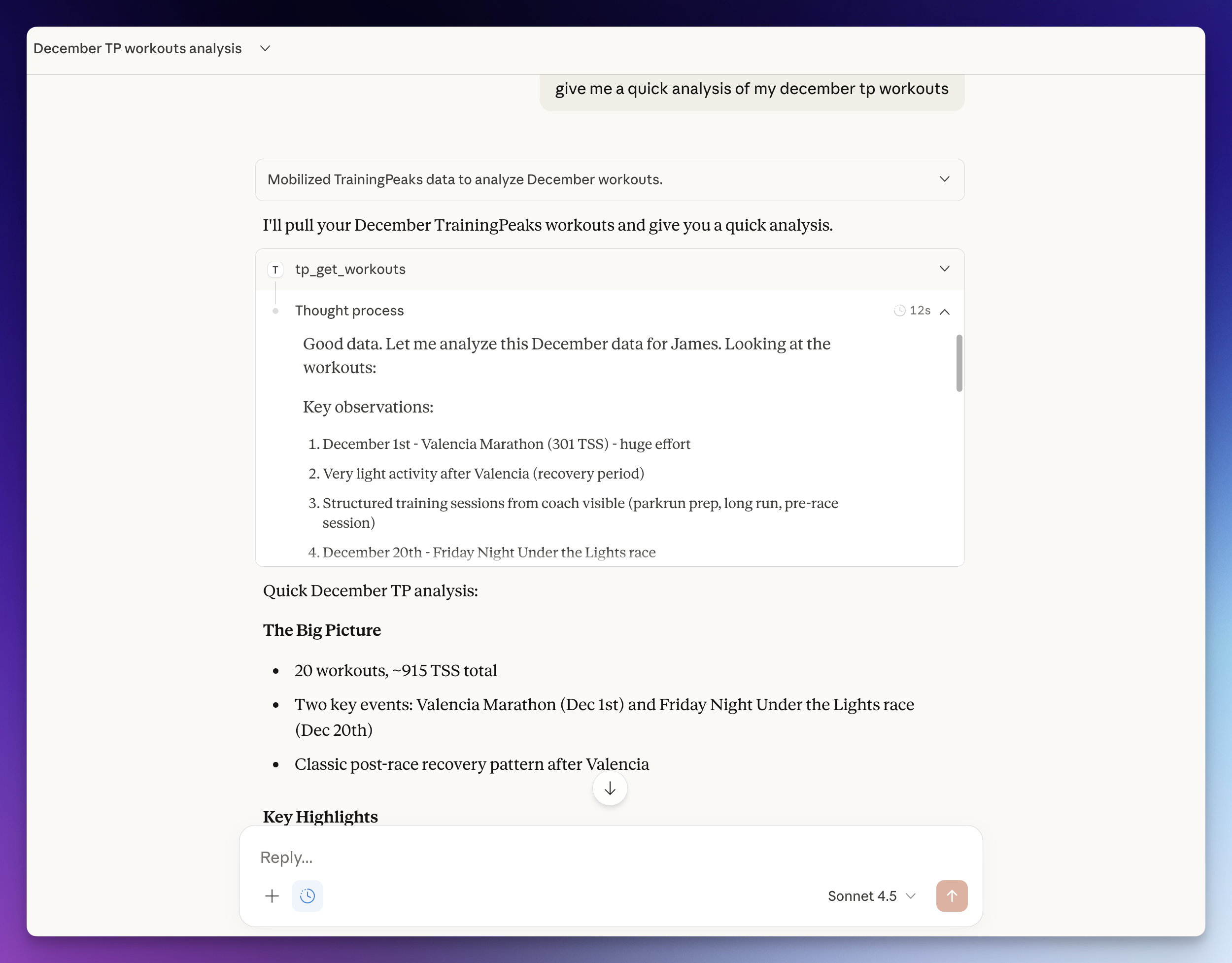
Ask your AI assistant questions like:
"Compare my FTP progression this year vs last year"
"What was my TSS ramp rate in the 6 weeks before my best 20-min power?"
"Am I ready to race? Show my form trend and recent workout quality"
"Which days of the week do I typically train hardest?"
"Find weeks where I exceeded 800 TSS and show what happened to my form after"
Features
Tool | Description |
| Query workouts by date range (planned and completed) |
| Get detailed metrics for a single workout |
| Compare power PRs (5sec to 90min) and running PRs (400m to marathon) |
| Track CTL, ATL, and TSB (fitness, fatigue, form) |
| See personal records set in a specific session |
| Re-authenticate if your session expires (extracts fresh cookie from browser) |
Setup Options
Option A: Auto-Setup with Claude Code
If you have Claude Code, paste this prompt:
Claude will handle the installation and guide you through authentication step-by-step.
Option B: Manual Setup
Step 1: Install
Step 2: Authenticate
Option A: Auto-extract from browser (easiest)
If you're logged into TrainingPeaks in your browser:
macOS note: You may see security prompts for Keychain or Full Disk Access. This is normal - browser cookies are encrypted and require permission to read.
Option B: Manual cookie entry
Log into app.trainingpeaks.com
Open DevTools (
F12) → Application tab → CookiesFind
Production_tpAuthand copy its valueRun
tp-mcp authand paste when prompted
Other auth commands:
Step 4: Add to Claude Desktop
Run this to get your config snippet:
Edit ~/Library/Application Support/Claude/claude_desktop_config.json (macOS) or %APPDATA%\Claude\claude_desktop_config.json (Windows) and paste it inside mcpServers. Example with multiple servers:
Restart Claude Desktop. You're ready to go!
Tool Reference
tp_get_workouts
List workouts in a date range. Max 90 days per query.
tp_get_workout
Get full details for one workout including power, HR, cadence, TSS.
tp_get_peaks
Get ranked personal records. Bike: power metrics. Run: pace/speed metrics.
Bike types: power5sec, power1min, power5min, power10min, power20min, power60min, power90min
Run types: speed400Meter, speed1K, speed5K, speed10K, speedHalfMarathon, speedMarathon
tp_get_fitness
Get training load metrics over time.
Returns daily CTL (chronic training load / fitness), ATL (acute training load / fatigue), and TSB (training stress balance / form).
tp_get_workout_prs
Get PRs set during a specific workout.
What is MCP?
Model Context Protocol is an open standard for connecting AI assistants to external data sources. MCP servers expose tools that AI models can call to fetch real-time data, enabling assistants like Claude to access your Training Peaks account through natural language.
Security
TL;DR: Your cookie is encrypted on disk, exchanged for short-lived OAuth tokens, never shown to Claude, and only ever sent to TrainingPeaks. The server is read-only and has no network ports.
This server is designed with defense-in-depth. Your TrainingPeaks session cookie is sensitive - it grants access to your training data - so we treat it accordingly.
Cookie Storage
Platform | Primary Storage | Fallback |
macOS | System Keychain | Encrypted file |
Windows | Windows Credential Manager | Encrypted file |
Linux | Secret Service (GNOME/KDE) | Encrypted file |
Your cookie is never stored in plaintext. The encrypted file fallback uses Fernet symmetric encryption with a machine-specific key.
Cookie Never Leaks to AI
The AI assistant (Claude) never sees your cookie value. Multiple layers ensure this:
Return value sanitization: Tool results are scrubbed for any keys containing
cookie,token,auth,credential,password, orsecretbefore being sent to ClaudeMasked repr(): The
BrowserCookieResultclass overrides__repr__to showcookie=<present>instead of the actual valueSanitized exceptions: Error messages use only exception type names, never full messages that could contain data
No logging: Cookie values are never written to any log
Domain Hardcoding (Cannot Be Changed)
The browser cookie extraction only accesses .trainingpeaks.com:
Claude cannot modify this via tool parameters. The only parameter is browser (chrome/firefox/etc), not the domain. To change the domain would require modifying the source code.
Read-Only Access
This server provides read-only access to TrainingPeaks:
✅ Query workouts, fitness metrics, personal records
❌ Cannot create, modify, or delete workouts
❌ Cannot change account settings
❌ Cannot access billing or payment info
No Network Exposure
The MCP server uses stdio transport only - it communicates with Claude Desktop via stdin/stdout, not over the network. There is no HTTP server, no open ports, no remote access.
What This Server Cannot Do
Action | Possible? |
Read your workouts | ✅ Yes |
Read your fitness metrics | ✅ Yes |
Modify any TrainingPeaks data | ❌ No |
Access other websites | ❌ No (domain hardcoded) |
Send your cookie/token anywhere except TrainingPeaks | ❌ No |
Expose your cookie to Claude | ❌ No (sanitized) |
Open network ports | ❌ No (stdio only) |
Open Source
This server is fully open source. You can audit every line of code before running it. Key security files:
src/tp_mcp/auth/browser.py- Cookie extraction with hardcoded domainsrc/tp_mcp/tools/refresh_auth.py- Result sanitizationtests/test_tools/test_refresh_auth_security.py- Security tests
Authentication Flow
The server uses a two-step authentication process:
Cookie → OAuth Token: Your stored cookie is exchanged for a short-lived OAuth access token (expires in 1 hour)
Automatic Refresh: Tokens are cached in memory and automatically refreshed before expiry
This means:
You only need to authenticate once with
tp-mcp authAPI calls use proper Bearer token auth, not cookies
If your session cookie expires (typically after several weeks), use
tp_refresh_authin Claude or runtp-mcp authagain
Development
License
MIT